 Guides
Guides
Measuring Compliance with standards is easy right?
Checking an environment configuration is one of those things where it’s easy to say and harder to do. If we take the cyber essentials standard and look at the requirements, they are quite different from say the CIS baselines. This alone makes for some fun, let’s investigate this further:
CIS baselines are based on a specific component e.g., Windows Server or Windows client and is contextually aware of roles: e.g., Domain Controller vs Member Server.
Is this registry key set?
(L1) Ensure ‘Turn off real-time protection’ is set to ‘Disabled’
hkey_local_machine\software\policies\microsoft\windows defender\real-time protection\disablerealtimemonitoring
The cyber essentials standard is agnostic:
The CIS baseline is asking on Windows Server 2022 is this registry key set, whereas cyber essentials is asking is antimalware deployed (A) and then if it is set to scan files automatically and update daily.
Now we could use the following command on modern Windows systems:
Get-CimInstance -Namespace root/SecurityCenter2 -ClassName AntivirusProduct
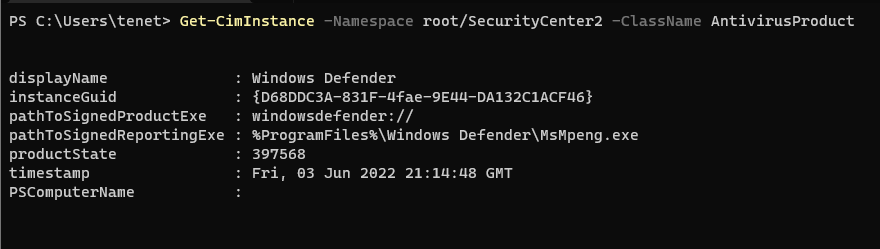
Now we know that defender is in use we could use the following cmdlet:
Get-MpComputerStatus
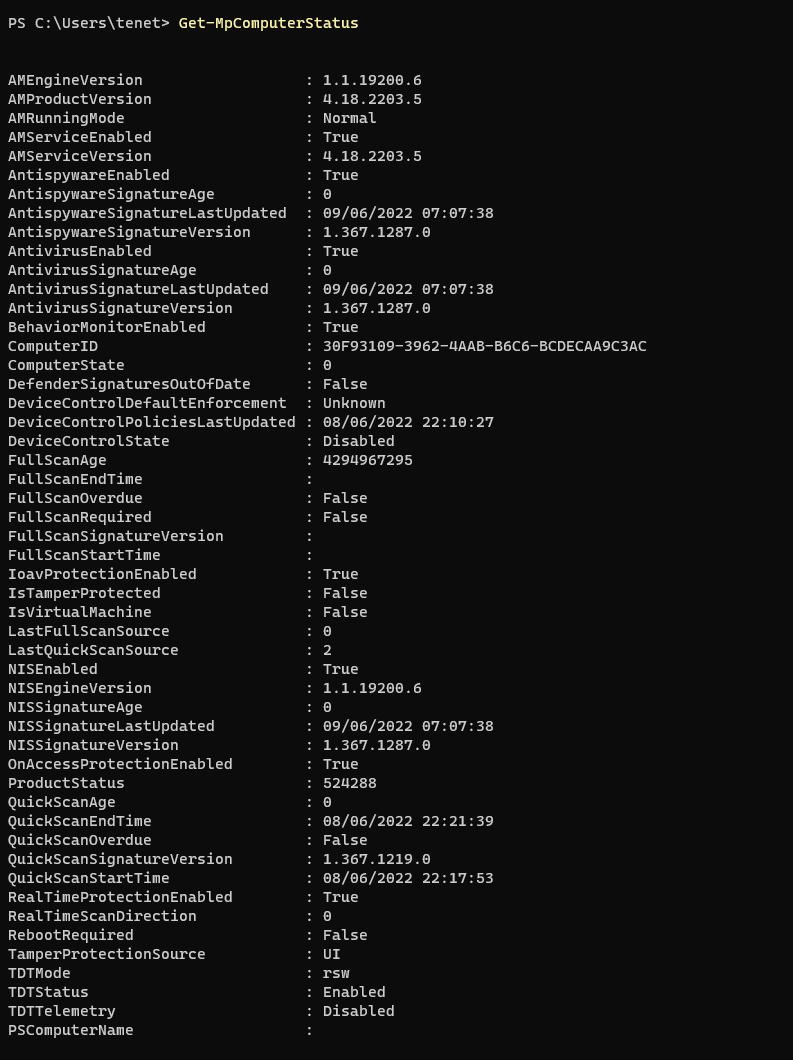
So great, we can run PowerShell here, on a single device that is easy. But there’s complexity in the world of technology. What if?
- The devices are many?
- They are not all part of a single domain?
- What if they aren’t using defender? If so, is there a console we can check?
- Are they managed via MDM? Could we use this to check?
- What about BYO devices?
In larger environments with diverse technology sets you may find that you need to adopt an approach for discovery, inventory and audit that leverages a range of technologies and methods. An example of this might be:
- Using RMM tools
- Using vulnerability scanning tools (e.g., Nessus)
- Using Group Policy
- Using EDR toolsets
- Using asset management and inventory tools
- Using scripts (WINRM/PowerShell/Bash/Python)
Now using MDM tools like intune we could create a custom compliance policy:
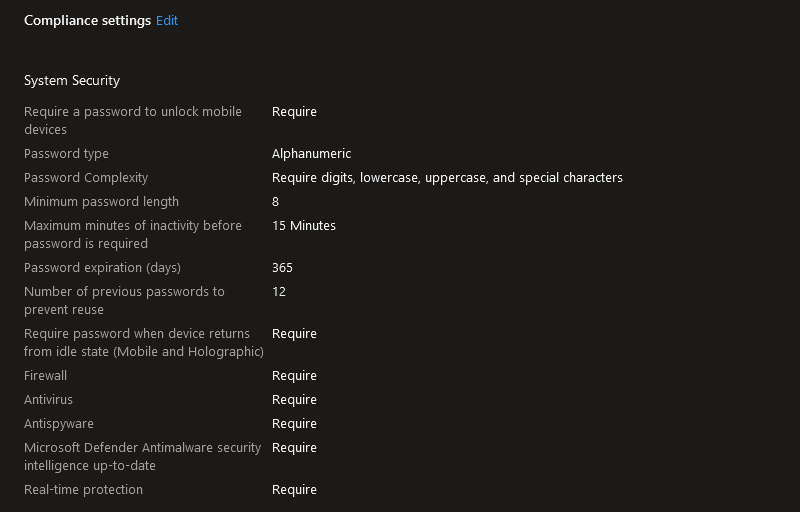
However we need to recognise a few things:
- This will only cover the scope of management for devices in intune, it won’t include servers for example.
- This does not cover every element to the Cyber Essentials standard.
Lastly if you are focusing on Cyber Essentials as a target rather than having well managed and secure devices you probably are missing the point a bit. However demonsrating to yourself and to an assessor for Cyber Essentials plus is important so it’s good to recognise the tools and methods you can use to do this.
Regarding complexity it really depends on your organisation’s technology estate and management platforms and capabilities. Sometimes this task may be simple, if all servers are in a domain and all endpoints are managed via Intune then this may be simple. But if you have 5 domains, 6 virtualisation platforms, BYO, unmanaged smart phones, and tablets and loads of Linux and Windows distributed servers (not domain joined etc.) you may find this task is rather complex. In this complex model you will need to leverage cross domain and product capabilities to get the data you need and configuration manage any remedial changes you require, but don’t worry I’ve not even started to talk about cloud services yet, I’ll save that for another day!








