 Vulnerabilities
Vulnerabilities
Regarding: CVE-2023-23397
This is a fast publish, use at own risk.
See guidance from Microsoft: CVE-2023-23397 – Security Update Guide – Microsoft – Microsoft Outlook Elevation of Privilege Vulnerability
If you need to mitigate the latest Outlook vulnerability which abuses an SMB/WebDav call using the Calendar invite feature you can consider the following:
# Update Office 365 Click to Run and Disable WebDav Client
# This should be run from userland
# GUI MODE Update
#& 'C:\Program Files\Common Files\microsoft shared\ClickToRun\OfficeC2RClient.exe' /update user
#Silent Office Update #Forced Shutdown
& 'C:\Program Files\Common Files\microsoft shared\ClickToRun\OfficeC2RClient.exe' /update user displaylevel=false forceappshutdown=true
# If you can't patch for whatever reason you can consider disabling webdav
# This should be run from HIGH PRIV/SYSTEM (Disables WebDav Client)
Get-Service -Name WebClient
Stop-Service -Name WebClient
Set-Service -Name WebClient -StartupType Disabled
Get-Service -Name WebClient
Hope this helps some people! use at own risk etc. (disabling WebDAV client may break business critical processes)
Detection
Ok this is NOT the best KQL query in the world but if you want to detect on egress on PUBLIC IP here is an idea:
/// Hunt for NON PRIVATE SMB Traffic
// as per CVE-2023-23397 and other SMB/SMB Relay Attacks
// please note this will not cover webdav to 443 or other ports
// custom alert (check every hour)
// thanks @gor_zilla for the ipv4_us_private(tostring())
DeviceNetworkEvents
| where Timestamp > ago(1h)
| where RemotePort == 445
| where not(ipv4_is_private(tostring(RemoteIP)))
| where RemoteIP != "::1"
| where RemoteIP != "127.0.0.1"
| where RemoteIPType != "Private"
| sort by Timestamp desc
Feel free to write a more optimal version, this is rough and ready to hunt for the common threat actor activity of egress to a non private IP (the RemoteIP checks are not efficient, I had to add them because the IPTYPE field was not on all networkevents)
You can then create a custom detection:
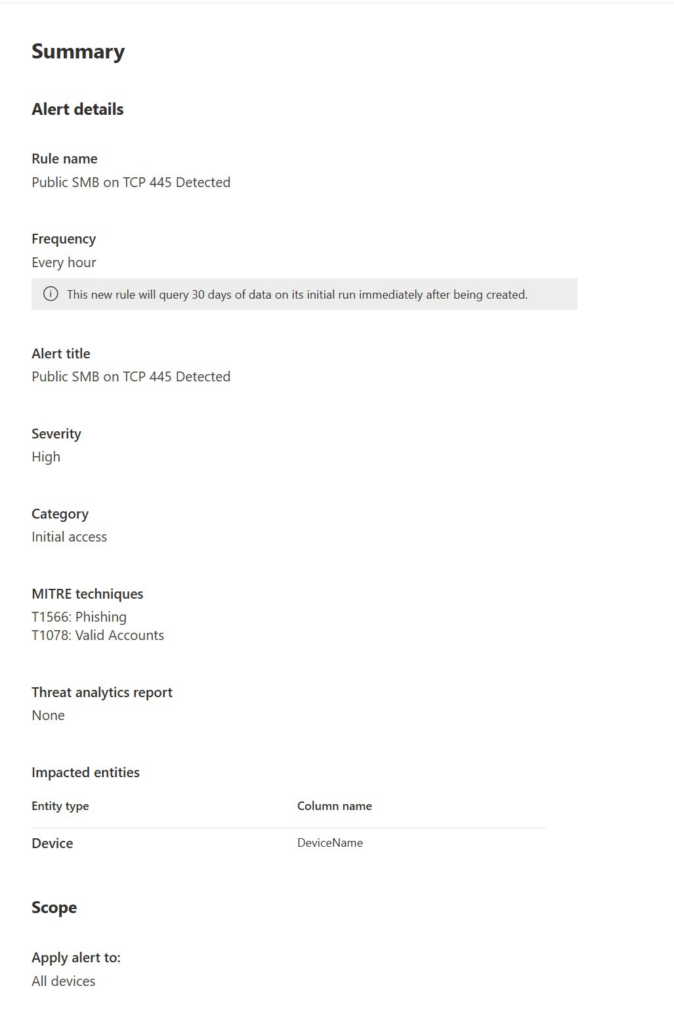
Feel free to write better / different queries, this is jus an example to help people think about detection.
We can also look for WebDav Client calling Public IPs
// Hunt for WebDav Traffic
// as per CVE-2023-23397
// WebDav Client Detection
// custom alert (check every hour)
DeviceNetworkEvents
| where Timestamp > ago(1h)
| where InitiatingProcessFileName contains "rundll32"
| where InitiatingProcessParentFileName contains "svchost"
| where InitiatingProcessCommandLine contains "davsetcookie"
| where not(ipv4_is_private(tostring(RemoteIP)))
| where RemoteIP != "::1"
| where RemoteIP != "127.0.0.1"
| where RemoteIPType != "Private"
| sort by Timestamp desc again use at own risk, make it better, share what you come up with etc. be safe!








