CTF
CTF
Abusing AdminSDHolder to enable a Domain Backdoor
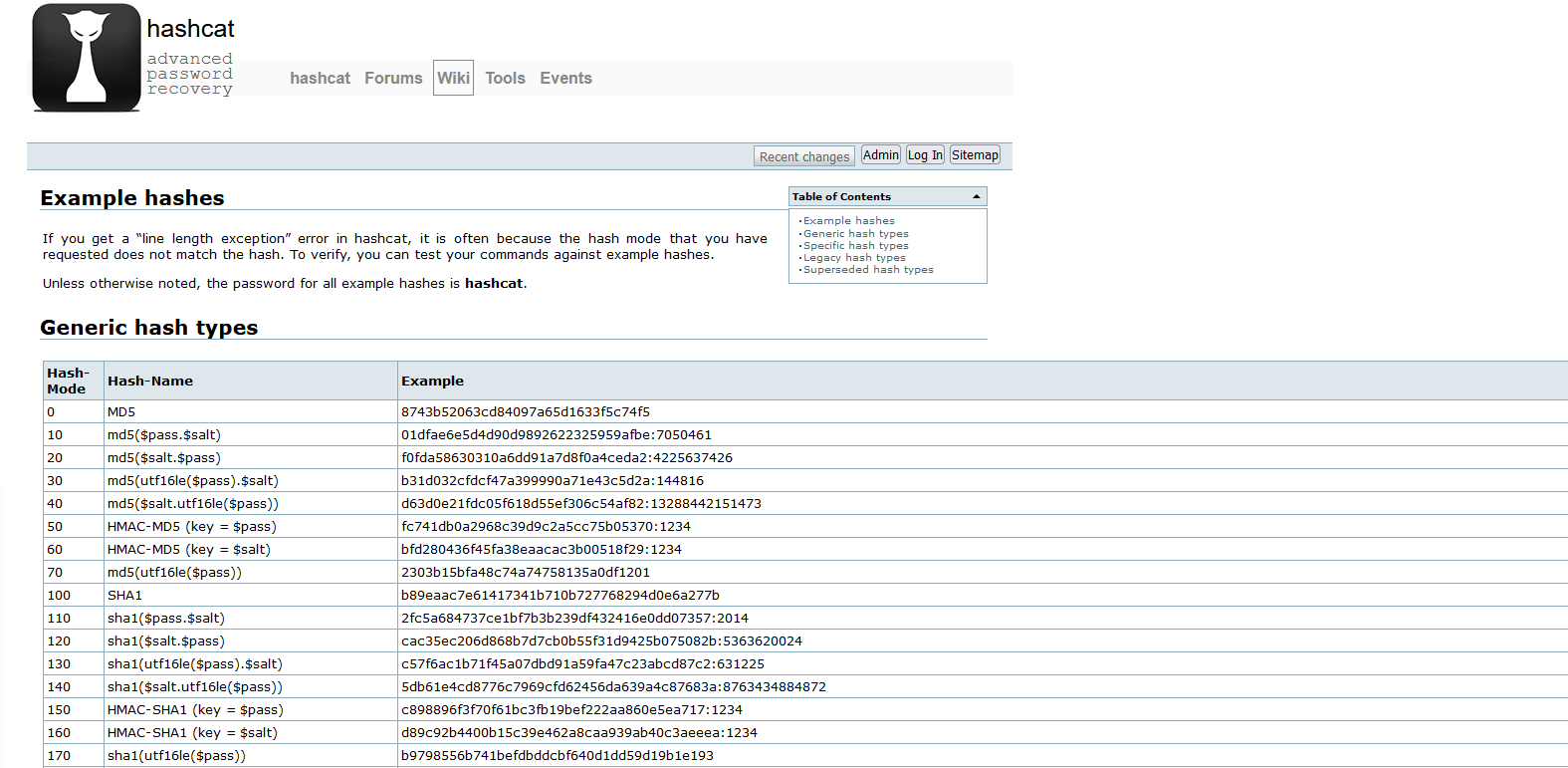
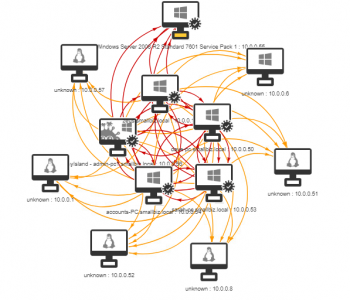
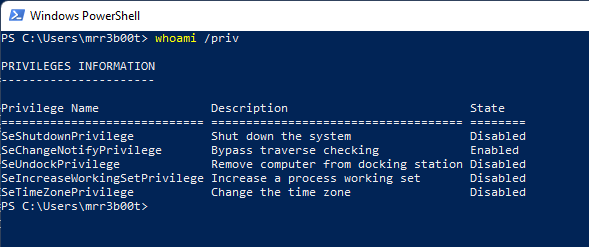
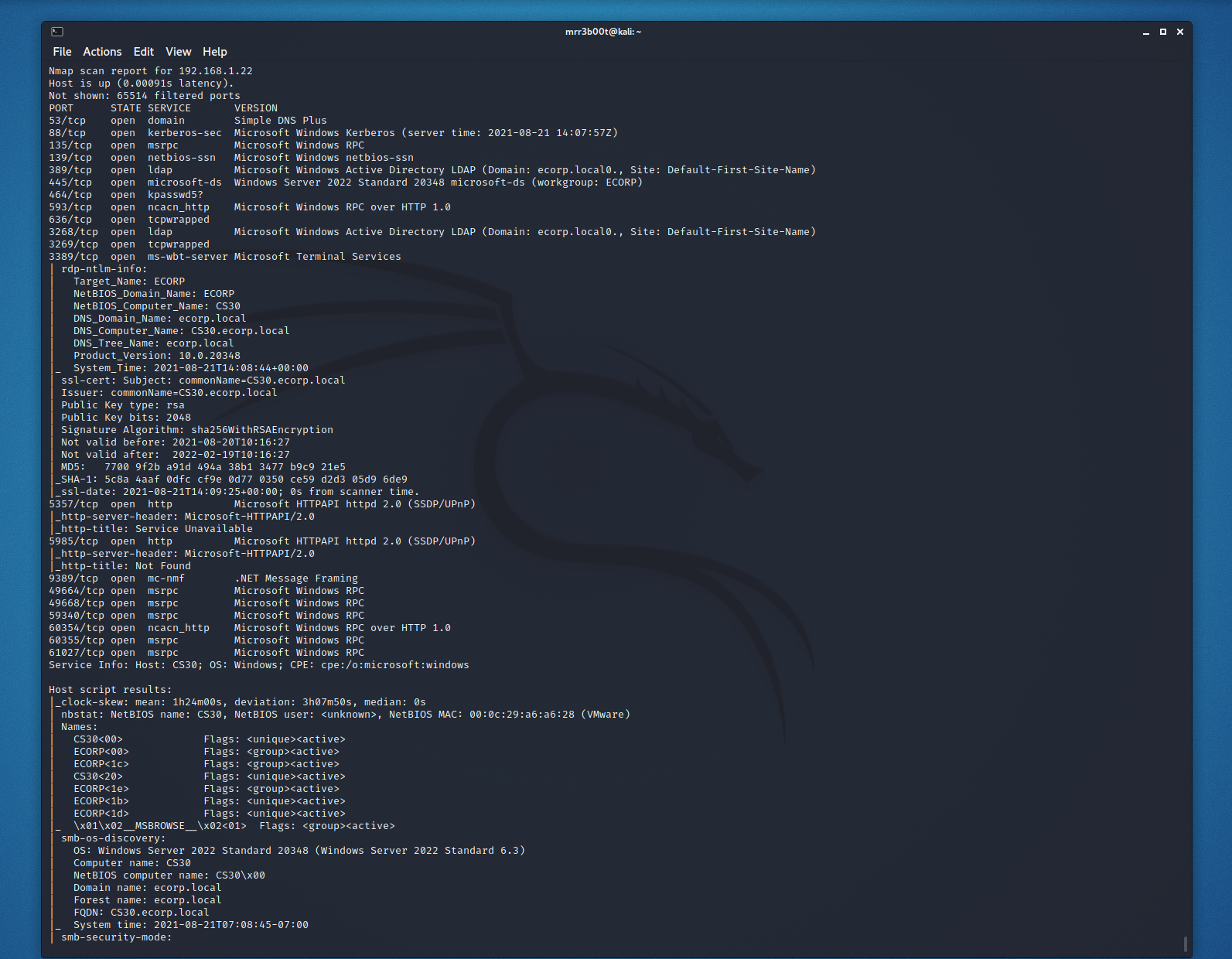
If we have high privilege access to a domain, we will likely want to establish persistence with high privilege access. One mechanism to do this is to assign ourselves permissions to the adminSDHolder object in active directory:
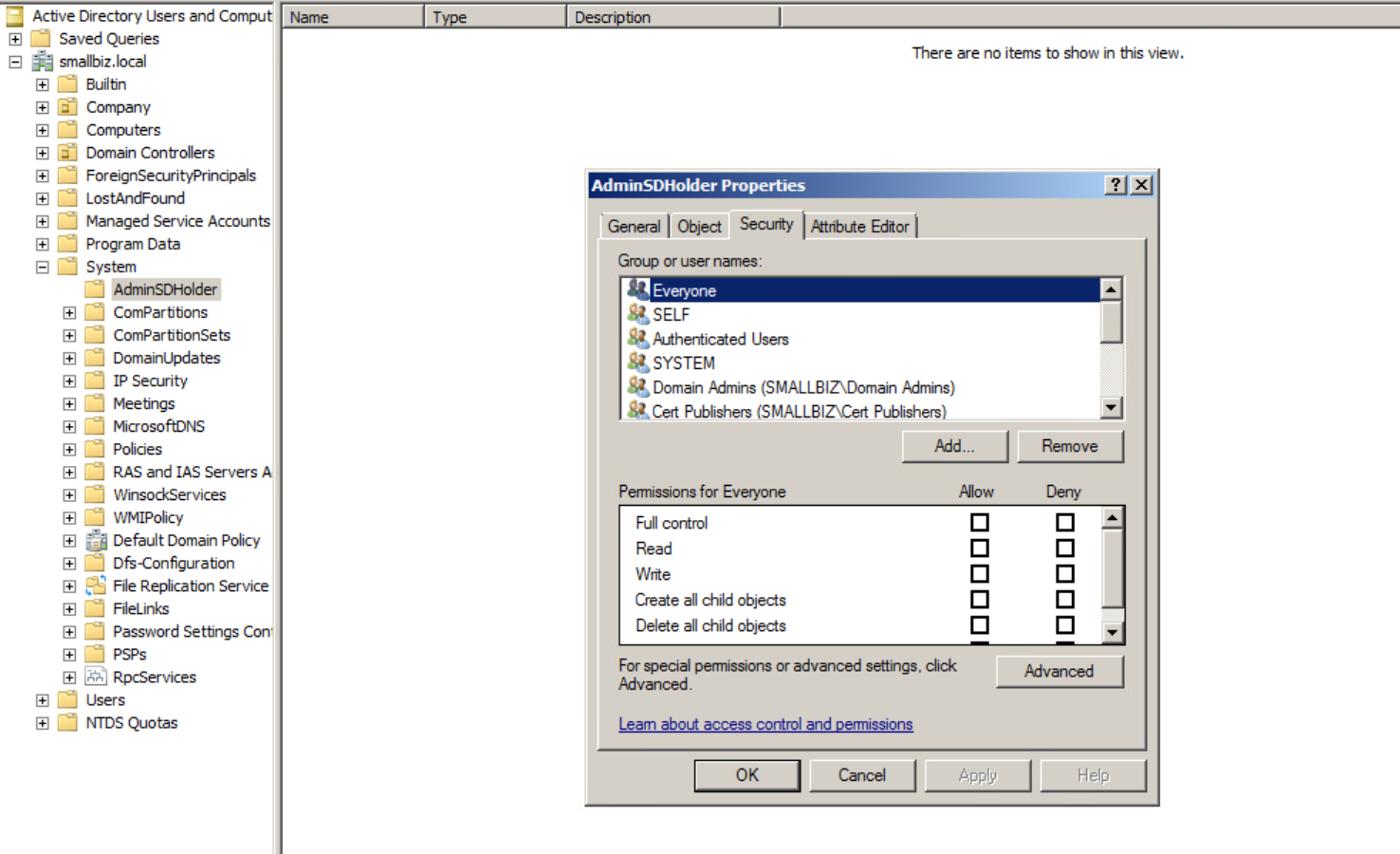
Here we have the default adminSDHolder permissions. We are going to add our user “low” in here with modify or full control permissions: Read more “Abusing AdminSDHolder to enable a Domain Backdoor”