 Defense
Defense
Ok this assumes you know how to get the NTDS.DIT and SYSTEM registry hive out from a domain controller, if you don’t go looking, we might have blogged a few ways to do that! Now then, firstly, let’s Install DSInternals. From PowerShell 5 onwards you can simply run:
|
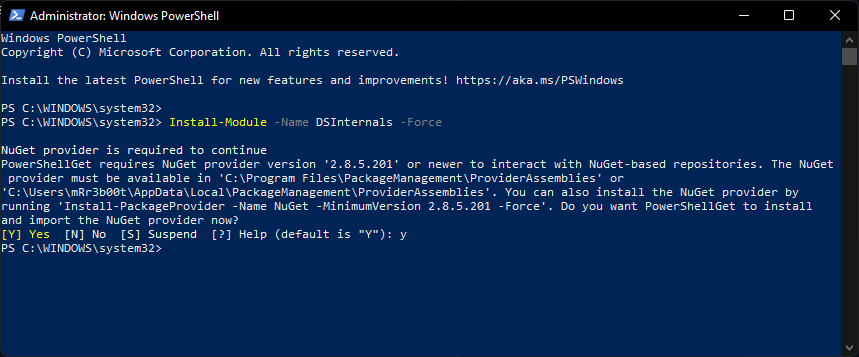
You will likely need to set your execution policy:
| Set-ExecutionPolicy -ExecutionPolicy Unrestricted |
Now to dump the hashes we use:
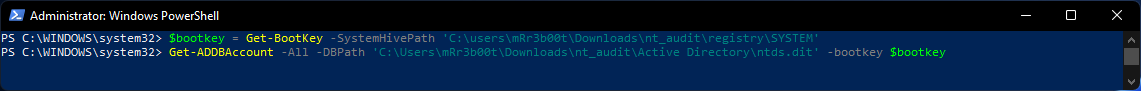
| Get-ADDBAccount -All -DBPath ‘C:\Users\mRr3b00t\Downloads\nt_audit\Active Directory\ntds.dit’ -bootkey $bootkey |
However, we need the bootkey from the registry hive!
So that’s easy because DSInternals gets that using the Get-BootKey cmdlet:
Now once we execute this, we will get hashes from the domain users (and their history). Now we are going to focus on NTHASH rather than LM but feel free to mod the script:
| Set-ExecutionPolicy -ExecutionPolicy Unrestricted
Set-PSRepository -Name ‘PSGallery’ -InstallationPolicy Trusted Install-Module -Name DSInternals -Force $bootkey = Get-BootKey -SystemHivePath ‘C:\users\mRr3b00t\Downloads\nt_audit\registry\SYSTEM’ $ntdsaudit = Get-ADDBAccount -All -DBPath ‘C:\Users\mRr3b00t\Downloads\nt_audit\Active Directory\ntds.dit’ -bootkey $bootkey foreach($object in $ntdsaudit){ If($object.NTHash.Count -ne 0){ $nthash = $object.NTHash | ConvertTo-Hex $hash = [String]::Join(”,$nthash); write-host $object.SamAccountName”,”$hash $hash | Out-File “C:\users\mRr3b00t\Desktop\cracking_hashes.txt” -NoClobber -Append } } |
So there’s some manual foo about byte arrays.. now DSInernals has some foo inside for making this easy:
| Set-ExecutionPolicy -ExecutionPolicy Unrestricted
Set-PSRepository -Name ‘PSGallery’ -InstallationPolicy Trusted Install-Module -Name DSInternals $bootkey = Get-BootKey -SystemHivePath ‘C:\users\mRr3b00t\Downloads\nt_audit\registry\SYSTEM’ $ntdsaudit = Get-ADDBAccount -All -DBPath ‘C:\Users\mRr3b00t\Downloads\nt_audit\Active Directory\ntds.dit’ -bootkey $bootkey $ntdsaudit | Format-Custom -View HashcatNT $ntdsaudit | Format-Custom -View HashcatNTHistory $ntdsaudit | Format-Custom -View JohnNT $ntdsaudit | Format-Custom -View JohnNTHistory |
Hell, that’s easy right! Now you have some hashes, load up “John The Ripper “of “Hashcat” and get cracking! Password audits are powerful things to use from a defensive position, get auditing, get educating, make those creds strong!
Check out the git repo here for the powershell examples: https://github.com/mr-r3b00t/DumpNTDS









