 Defense
Defense
Introduction
“Ransomware is a major issue!”
Hang on maybe we need to re-phrase that:
“Weak security postures are a major issue!”
or perhaps.. why not both!
I’ve been working with digital technology management for over 20 years, I started out when I was a kid (literally) fixing people’s PCs in their offices, removing malware, improving configurations, writing batch file menus, and playing games. As time has gone on technology has shrunk and continually become more and more of our everyday lives.
Back in 2003 I responded internally to MSBlaster, an SMB worm that had a devastating effect for the time, by today’s standards it was child play, however I remember saying “it’s a good job it didn’t delete everything whilst it was here.” (Or something very similar. Post NACHI/Blaster my friends and I were talking about how worse it could get. Fast forward in time and it’s much worse. Yet when I look at networks, they don’t look very different to how they did back in the 2000s.
Despite a multi-billion-dollar cyber security industry, it seems daily that organisations are succumbing to “cyber-attacks” which commonly include ransomware. Why are they successful and why are they so impactful? Well, let’s take a look!
State of Network Security Posture
I’ve been auditing a fair number of active directories recently, but I’ve been in hundreds of companies, whilst that doesn’t mean my view is “the view” but it will at least give a view from my perspective.
To undertake this task, we’ve standardised using a tool called Ping Castle, this doesn’t cover everything, but it gives a good and efficient insight into the organisation’s security posture.
90% of all organisations we’ve reviewed so far (across a range of verticals) have a similar pattern:
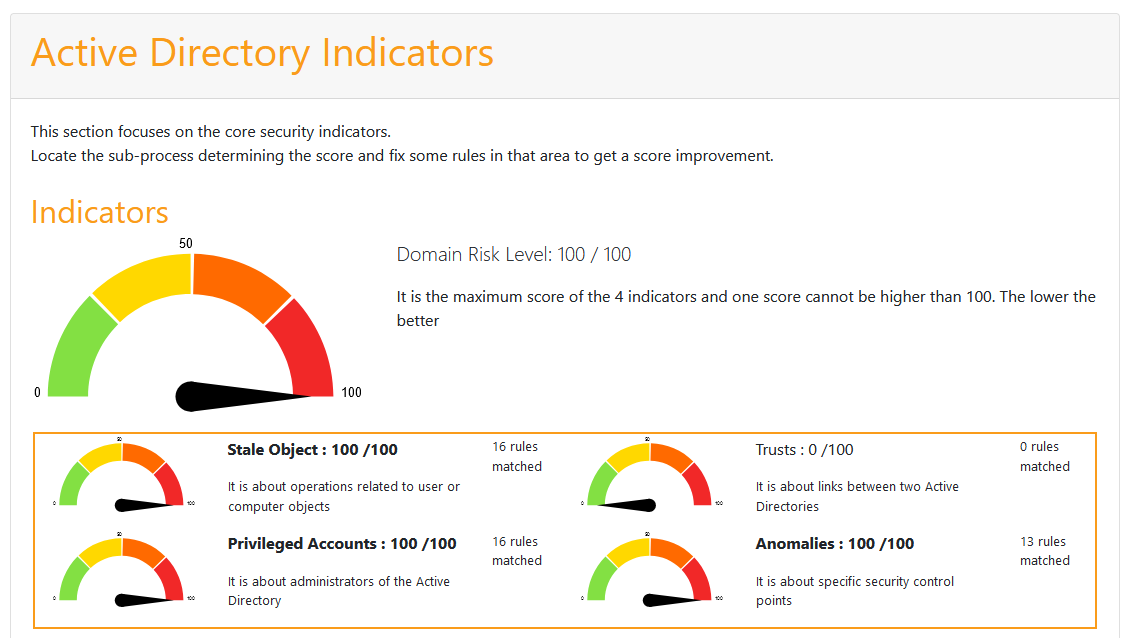
I’m not going to go into every area but let’s jus say here the common findings from both the audits and consulting work we conduct, many networks:
- Have primary forest, domain joined backup services
- Have weak passwords for users, administrators, and service accounts
- Are vulnerable to kerberoasting
- Have passwords in clear text (either in GPP, user description fields, file servers etc.)
- Have insufficient auditing, monitoring, and alerting
- Rely largely on signature-based detections
- Do not have dedicated specialist cyber security staff
- There is little to no segmentation inside the network
- Are vulnerable to MDNS/LLMR attacks
- Have unpatched systems with known vulnerabilities, often with RCEs
- Do not have a planned, robust, and practised incident response process (or procedures)
- Have not purposefully hardened computer networks and systems
- Lack egress filtering, content inspection/HTTPs inspection etc.
- Do not have a dedicated SOC capability
- Most networks have high privilege accounts with total network access
Overall, the posture of network/organisations are largely very weak, even the stronger postured orgs tend to have significant capability gaps etc. (remember this is a generalisation, it won’t fit every scenario/org etc.)
State of Ransomware
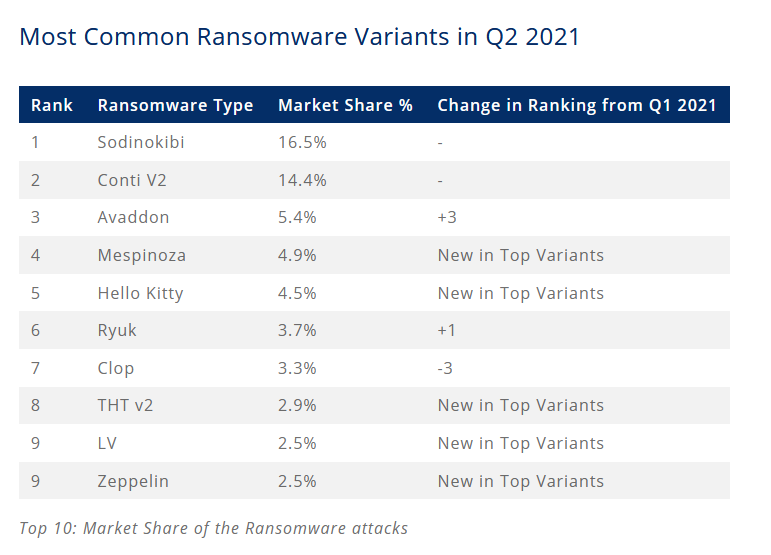
For this view we are going to use some snippets from Coveware:
We can also see here the trends of initial access vectors:
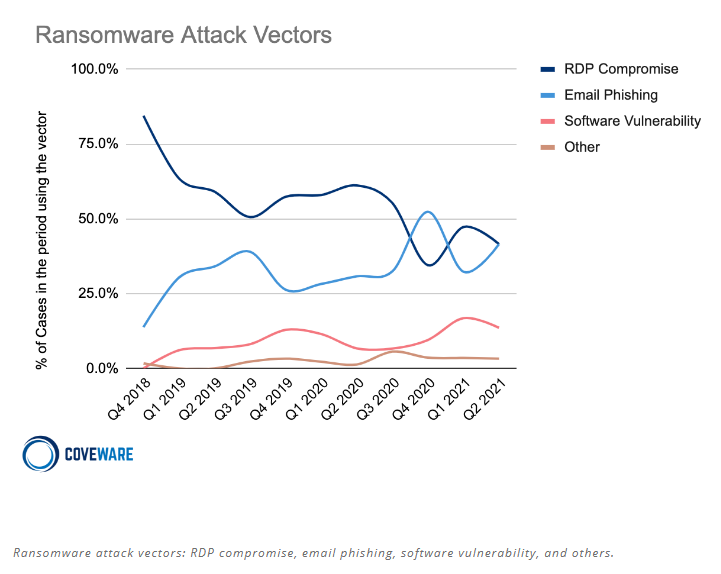
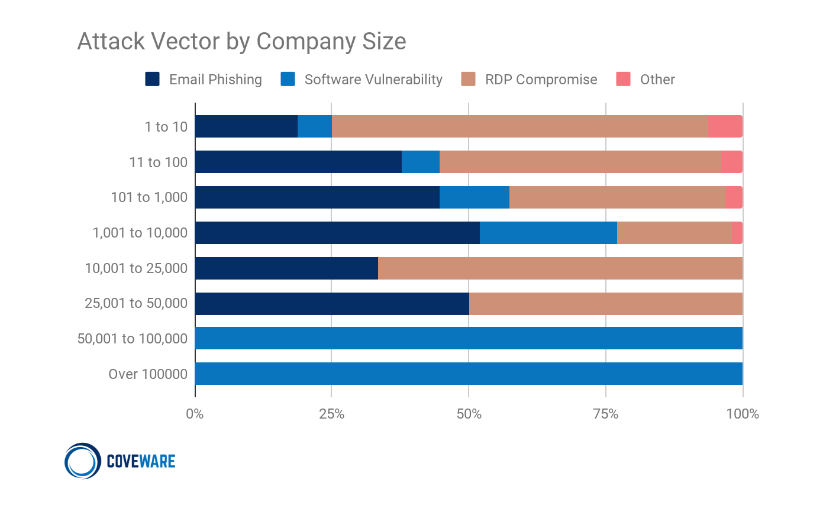
I’m not going to go into detail here, but we can see that REVIL and CONTI (we are going to analyse some of their tools later) are the most popular ‘groups’ of Ransomware activity, the initial access is mixed via RDP, Phishing and Vulnerability etc.
Typical Ransomware Kill Chains
So, we can dip a little bit more in the details, I’ve put together a list of some of the common methods used in a kill chain, for the purposes of this blog I’m not
Gaining Access
- Macro Enabled Document via Phish
- Malicious PDF via Phish
- Scripts via Phish
- HTA via Phish
- Remote Code Execution
- Valid Credentials
- RDP/Citrix Brute/Dictionary Attacks
- RDP/Citrix Access post credential harvest via Phish
- RDP/Citrix Credential Stuffing
- Purchased access via an initial access broker
- RCE Vulnerability in network edge device
- Valid Credentials
Initial access clearly needs to occur, but as you can see there’s a range of options.
It’s worth looking at the CISA top routinely exploited vulnerability list:
https://us-cert.cisa.gov/ncas/alerts/aa21-209a
(it’s similar to a list we put together for CV19 but its got a nice official logo so fill your boots)
Actions and Impact
Once access has been established this is where a whole host of activity occurs but the primary objectives here are:
- Escalate Privileges & Move Laterally
- Exfiltrate Sensitive Data
- Encrypt the backups and live datasets
The ultimate objective here is for the ransomware actors to get paid.
Law Enforcement
Cross border crime from a global landscape is a huge challenge. You can’t just bust down the door to a room with a criminal operator in if say they are in Iran, or Russia or well anywhere that isn’t inside the country/area of jurisdiction etc. I’m not going to talk a lot about law enforcement and ransomware but as you can probably guess, it’s a major challenge, that I don’t think the world planned for, is skilled to deal with (at the volume at least) or has the resources.
The hard truth
Ransomware Myths
“There are groups of highly advanced actors using customised tactics, techniques and procedures (TTPs) to take down highly defended networks”
Ransomware Reality
“Most networks are poorly segmented, weakly configured and poorly defended.”
Summary
Part 1 takes a look at some of the realities of modern network security postures alongside initial access and impacts of ransomware. This is a complicated problem, but from where I sit, there’s a key element here about defence. If we can’t defend out networks, deterring and disrupting, in my mind will largely be ineffective, it would be like trying to start a fight with the biggest bully with zero training, it’s not a strategy that I think leads to a good outcome!
Part 2 – Conti Analysis
Ok so hopefully we’ve got a high-level view of the targets/victims, the methods used to gain access, the state of the network’s security postures. This so far isn’t painting a great picture but let us look at some of a real-world ransomware actors TTPs, luckily the other day someone posted a bundle of intel from Conti. In the next post I’m going to look at what this tells us about the actors using the Conti services!









