Leadership
Leadership
Cyber Security Architecture
I remember (now it was a long time ago) when I worked in a support role and my dream job was being a technical architect, back in the warm and fuzzy days of no host-based firewalls, IPsec being something only MCPs knew about other than the networking team and when cybercrime was a shadow of how it is today.
It wasn’t until I had a few more notches under my belt when I realised that architecture in technology has different viewpoints, not only that but even the industry can’t agree on what things are or are not. That aside the reality is, is that architecture has different domains, specialisms, views, and viewpoints. I often find myself working across a whole range of areas, that is driven largely by specific customer requirements and scenarios (this is why I have a cool lab and lots of kit!)
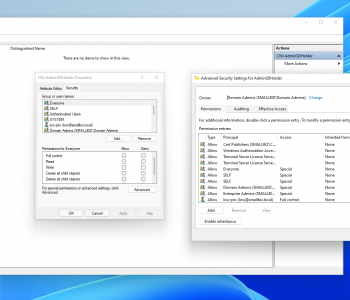
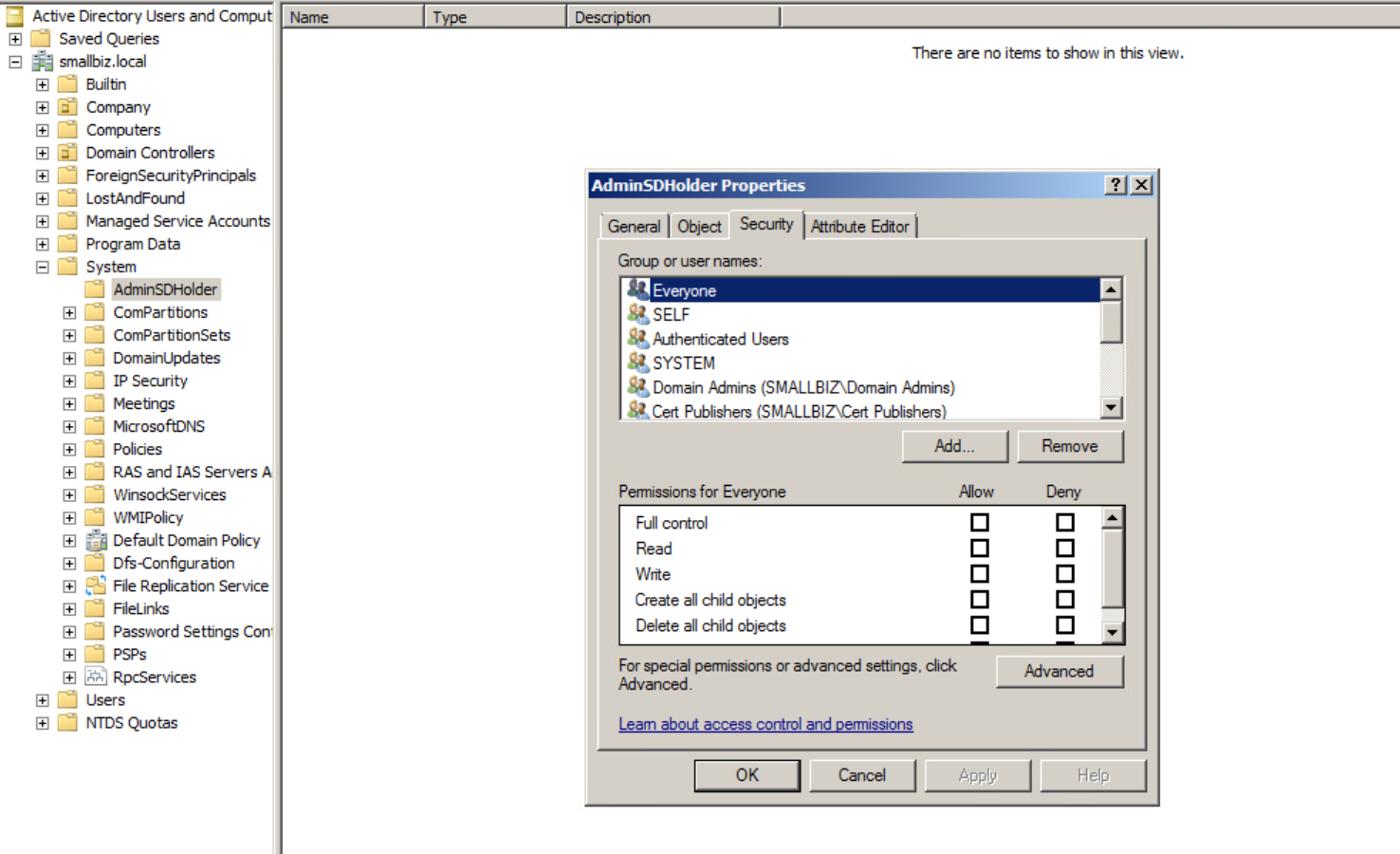
When we consider a business technology system it has risk and by nature cyber security in that view. To think of this not being the case would be odd because ultimately “business” is the highest abstraction, and let’s think about what makes up a business: Read more “Cyber Security Architecture”