 Defense
Defense
There’s a new CVE in town but don’t think it’s the only problem you get when you expose administrative interfaces to the wild west of the internet (yeeha or something). Let’s go on a quick exploration of what the world looks like with the help of our friends at Shodan and then let’s see the ramblings of Dan when looking at how benign enumeration and exploration of services can work. Let’s get started looking at the world, a quick face analysis on Shodan with vmware as a product shows a hit or two, what we are going to focus on is vCenter but you know.. you might want to review your attack surfaces so any exposed services (damn people expose some risky stuff!)
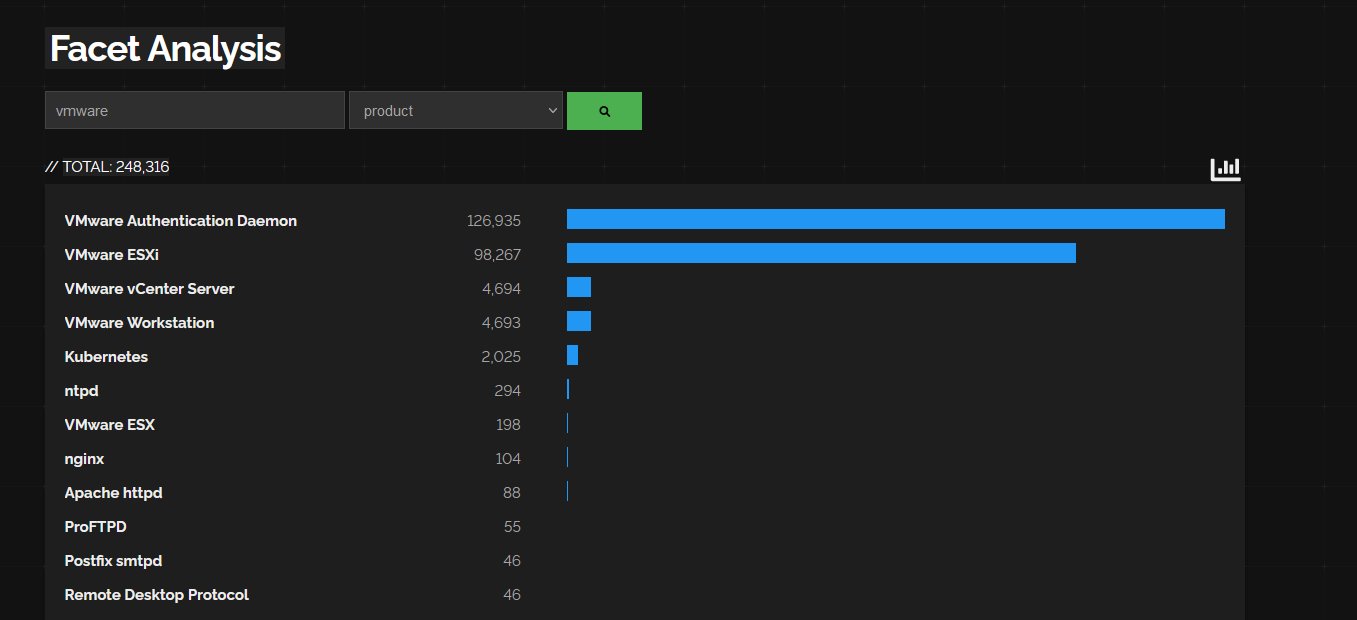
We then focus on vCenter:
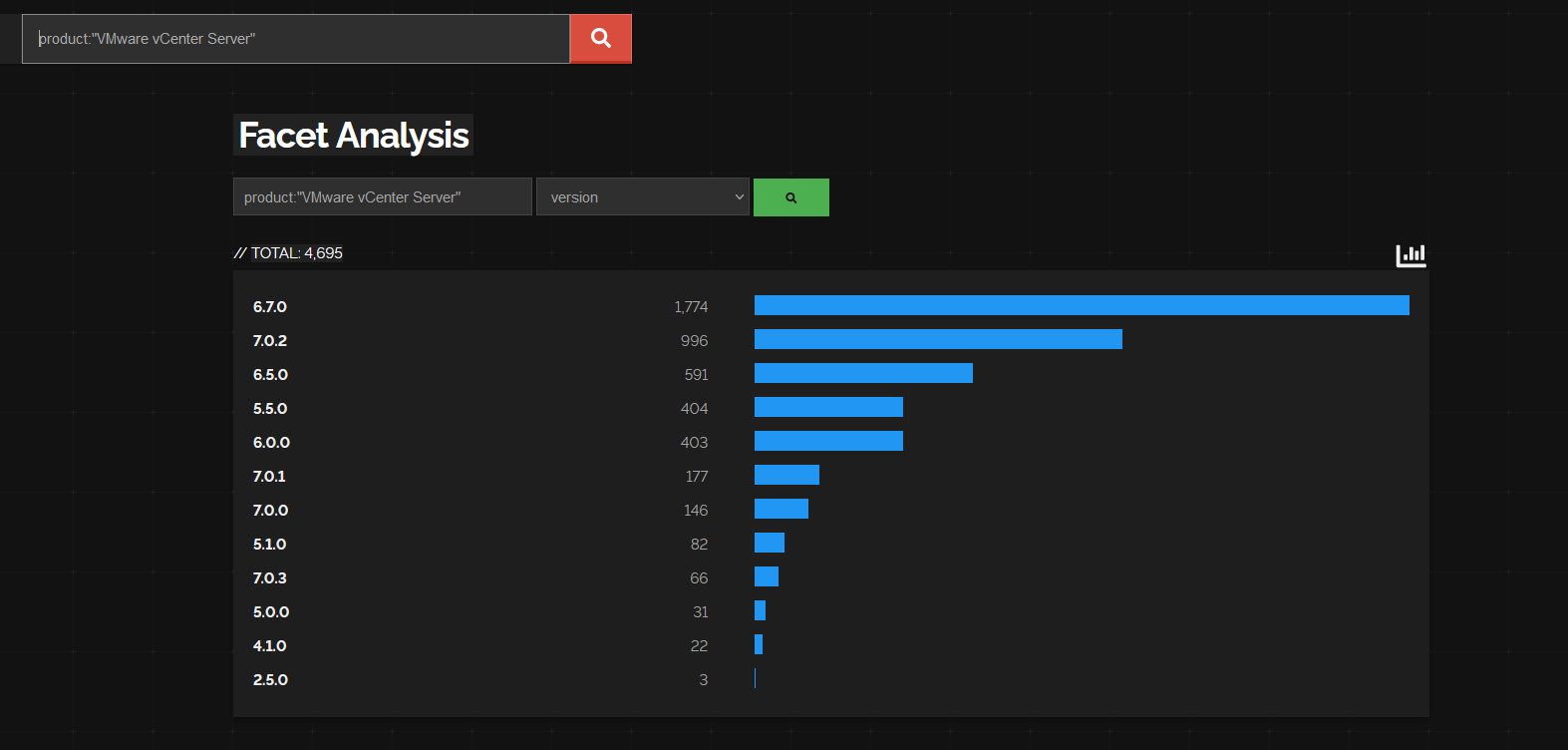
Shodan has a function to enumerate the versions of some products, so now we know there will be a benign manner of checking this. Now the summary versions here are high level, what we really want to know (from a goodie and baddie pov) is the build versions. Let’s see if we can Consider the HTTP packet world and see what goodies vcenter might be able to tell us! Next up we go on a bit of winding journey through Dan’s brain. This isn’t the first time I’ve looked at enumeration for vSphere but I’ll be honest, it may as well be. Let’s get some Burp Suite action going to see what we can see. We start by just having a play with HTTP but also, we want to read architecture documents and research etc. Search engines are your friend in this space.
Now the good part here is we know what we are looking for:
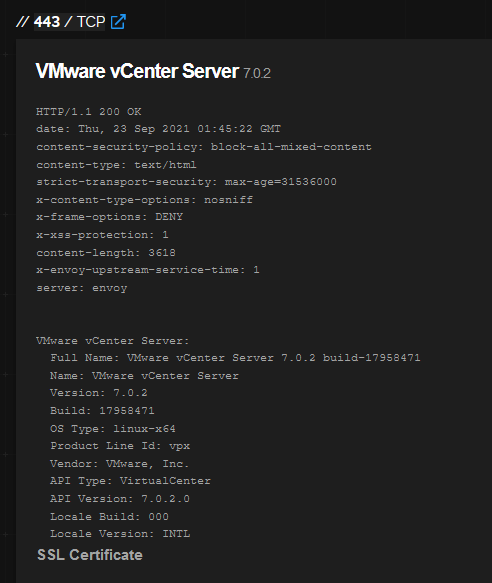
So I fire up burp and start to play around with connections to a vCenter server I have in the lab.
Now I know there’s both a web application and API sets on a vCenter service, but let’s explore in HTTP land as well as read (we can do both right!)
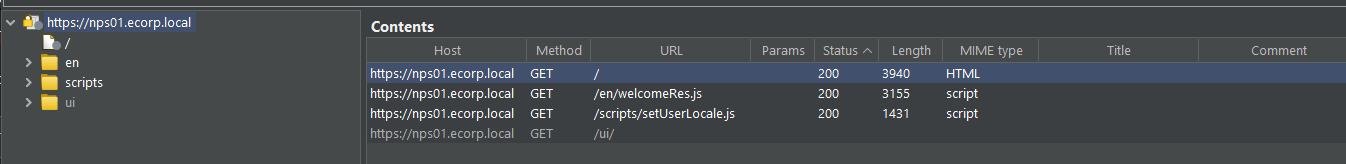
So, we get a connection to vCenter running then we manually start probing in the browser but also, we want to use content discovery. We are doing this from a completely unauthenticated perspective.
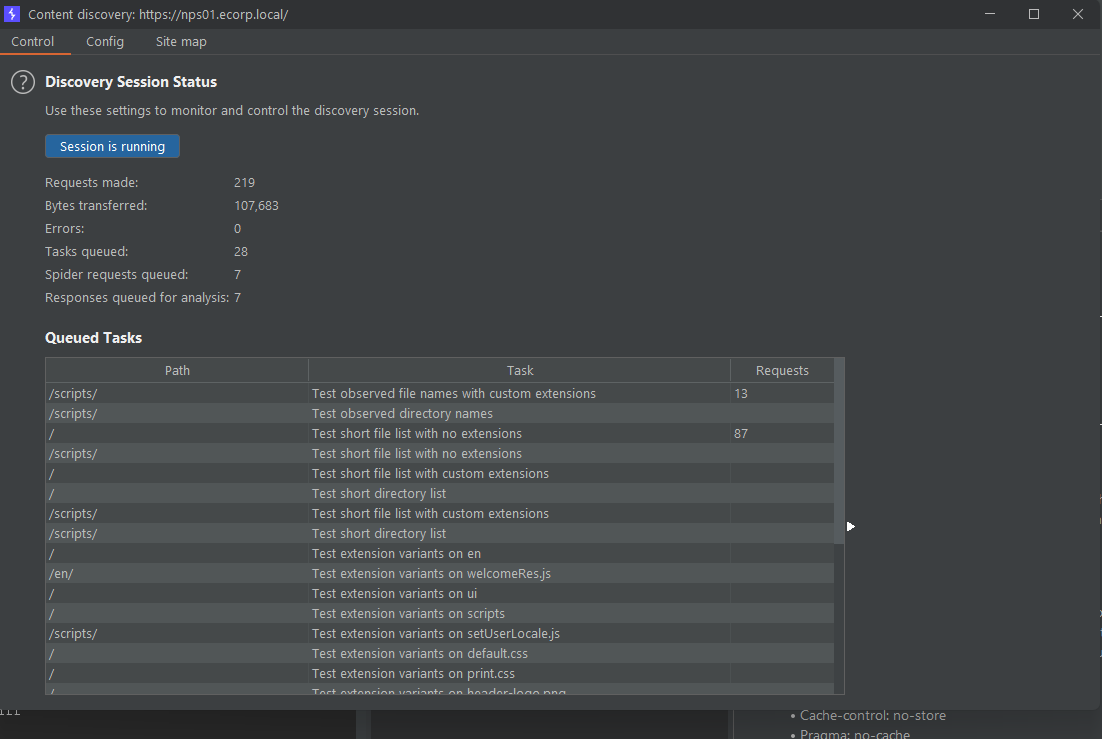
Whilst discovery runs, we run searches but can’t find any strings in the HTTP responses that look useful. We go exploring on the internet:
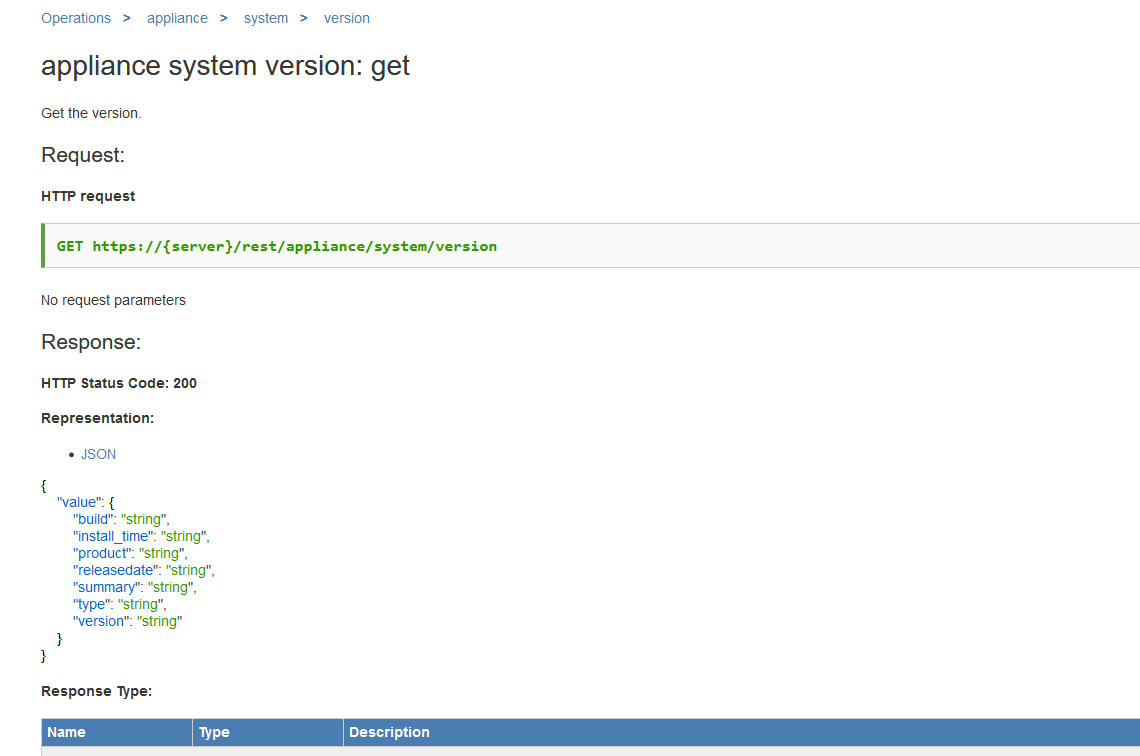
We find some API references which include build version information from the API. This endpoint however I believe requires authentication.
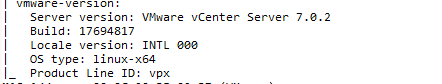
I also think about nmap, so we have a quick search and there’s an NSE – also because to test we need to do I run a quick scan using ZenMap:
Reading the NSE shows that there is a POST request to an endpoint with a SOAP payload.
I fire up repeater and modify the GET request and inject the SOAP payload:
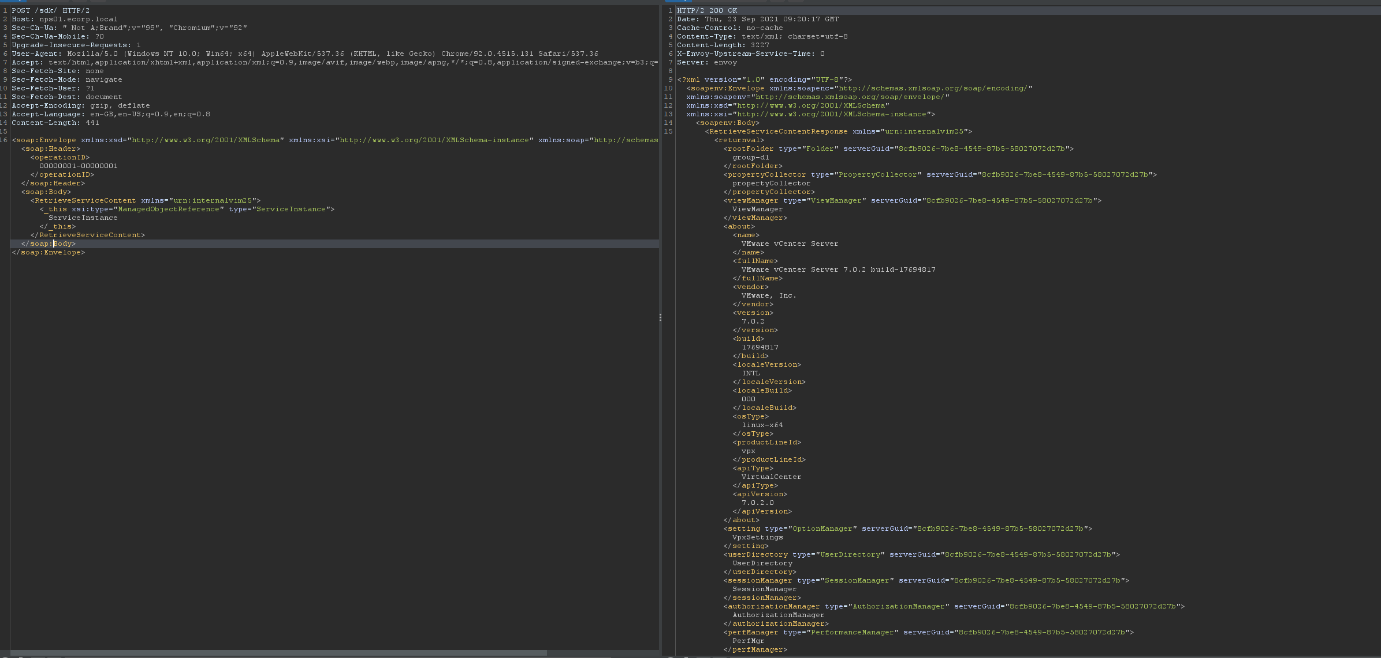
Kaplaa (Success in Klingon obvs!) we have a request. We can use burp to create a simple curl request for us! Now the POST request header contains a ton of params we probably don’t need so let’s bin the junk:
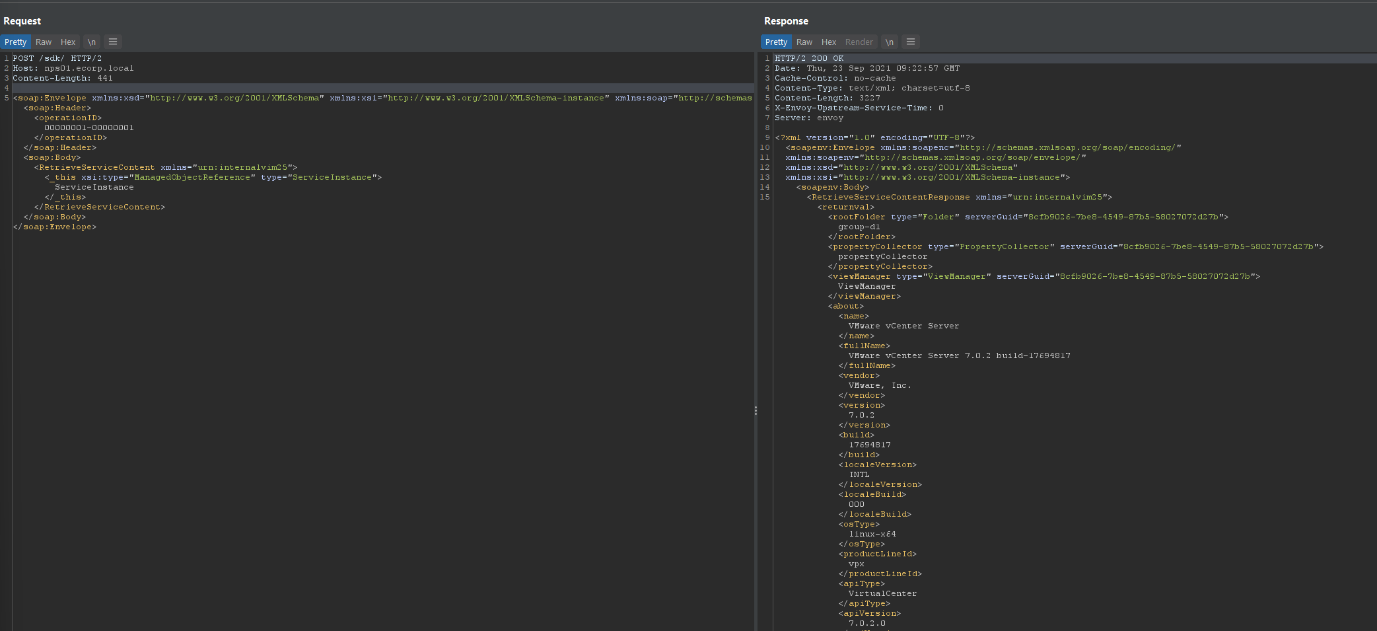
And now let’s grab the curl syntax:
| curl -i -s -k -X $’POST’ \
-H $’Host: nps01.ecorp.local’ -H $’Content-Length: 441′ \ –data-binary $'<soap:Envelope xmlns:xsd=\”http://www.w3.org/2001/XMLSchema\” xmlns:xsi=\”http://www.w3.org/2001/XMLSchema-instance\” xmlns:soap=\”http://schemas.xmlsoap.org/soap/envelope/\”><soap:Header><operationID>00000001-00000001</operationID></soap:Header><soap:Body><RetrieveServiceContent xmlns=\”urn:internalvim25\”><_this xsi:type=\”ManagedObjectReference\” type=\”ServiceInstance\”>ServiceInstance</_this></RetrieveServiceContent></soap:Body></soap:Envelope>’ \ $’https://nps01.ecorp.local/sdk/’ |
Perfect! We now have all the information we need to create a scripted benign ACTIVE scanner. I’ll leave that for the community to play with if they like, you could plug this into Nuclei with Axiom for mass scanning with a fleet if you were so included!
Key thing here, ideally, do not expose these interfaces to the internet, if you need them exposed look at controls such as WAFs, allow lists, vpns, reverse proxies etc.
Keep your systems patched there’s a new RCE (CVE-2021-22005), which looks fairly simple to exploit. Bad actors are already scanning the internet! Stay safe, until next time!






