 Defense
Defense
Introduction
This is part of a series I’m writing which is focusing on some of the core fundamentals of why cyber security is a business issue, why business leadership should care and invest in a good security posture and I’m looking at common security threats and ways you can combat these.
Now just because I said you are the CEO/A business leader doesn’t mean that I said I wasn’t going to talk about some of the details. Sure, you can delegate this but in a lot of organisations you may not have a CISO, the CTO might not want to admit some of this isn’t “on point” and well given the reality of the damage phishing can have to your business I figure a few details won’t hurt. The key aim for this post is to educate but also to raise some important questions that you can take to your organisation to start ensuring there is focus on a key area exploited by threat actors.
Phishing
Phishing comes in multiple shapes and sizes and can also be a starting point to lead to supply chain compromise which may in turn use phishing, valid accounts, and then external remote services (see it can get complicated real fast). So, let’s talk about phishing and what that is:
Phishing (or other computer aided social engineering) is where you receive an email from a threat actor that:
Tricks you into acting to disclosure sensitive information or take actions which will cause negative harm
To accomplish this the threat actor (baddie) might:
- Send you a malicious document that uses MACROS (application programming) to launch malicious code to give the threat actor control over your device
- Entice you through a malicious document or web url (hyperlink) to visit a site
- This site may ask you for your credentials
- The site may exploit a browser vulnerability by using a software vulnerability
- The site may create a browser hook (a browser script) to connect to the threat actor
- They might simply ask you in a convincing manner to act e.g.
- Send payment for an invoice
- Send money to help a friend
- Attempt to extort by claiming to have “hacked your webcam” or blackmail you claiming they have your browser history and will release it to friends and family if not paid
As you can see there’s a range of common threats relating to email and phishing (and other forms of communications including phones, SMS, social media etc.)
The threat is real
Anatomy of a “Cyber Attack”
Ok, so anyone that knows me will know I don’t particularly get on with calling everything “an attack”, however It’s common usage. It’s better to say cyber event or if you know it’s a negative event then “cyber incident” works for me. Now to do this we are going to look at the Mitre ATT&CK framework (it’s what all the cool kids do with their references in their blogs these days) over at https://attack.mitre.org/.
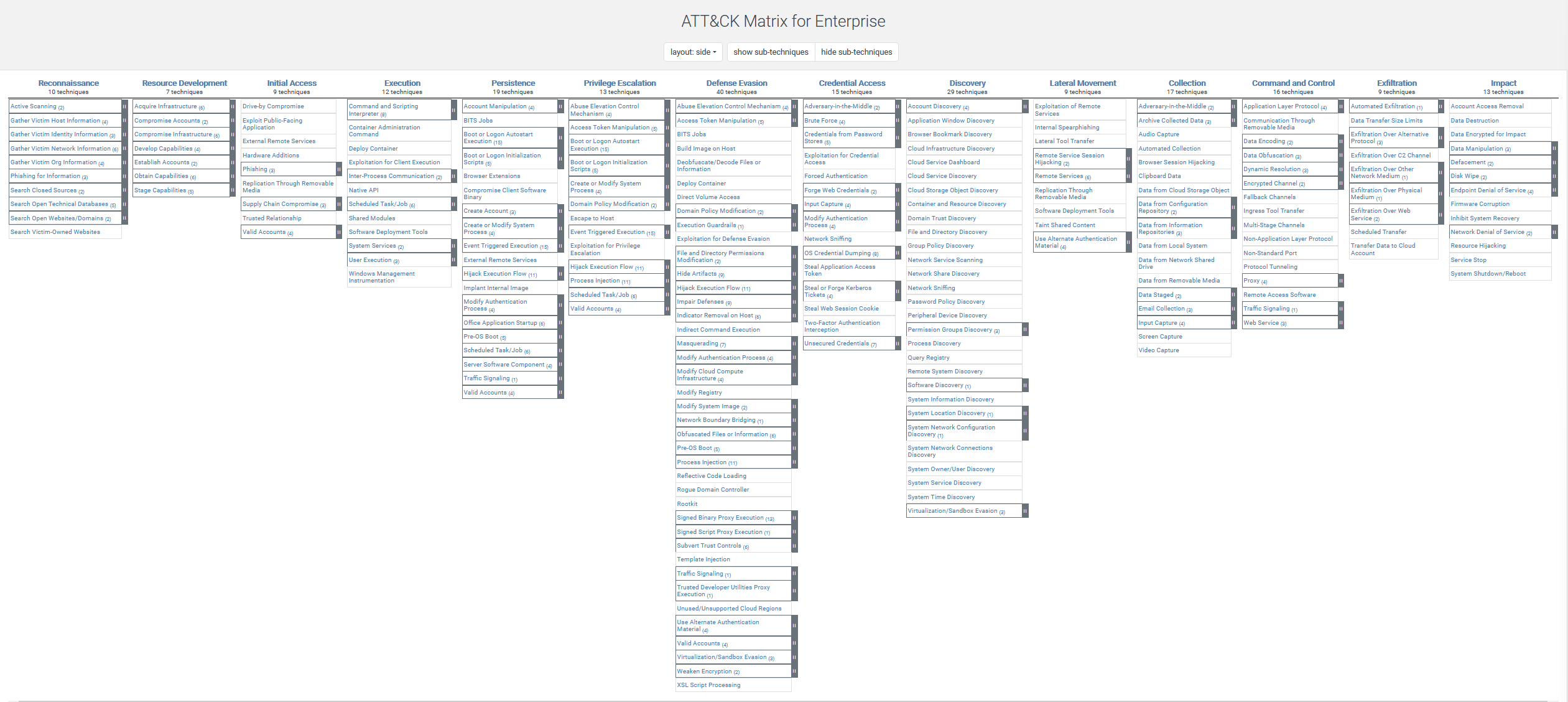
The ATT&CK framework provides a series of information on Tools, Techniques and Practises (TTPs) that are commonly used in cyber events and incidents. That’s quite in the weeds but I wanted to show this is grounded in industry bodies of knowledge and not just my opinion.
Now when we zoom into “initial access”, we are going to see PHISHING:
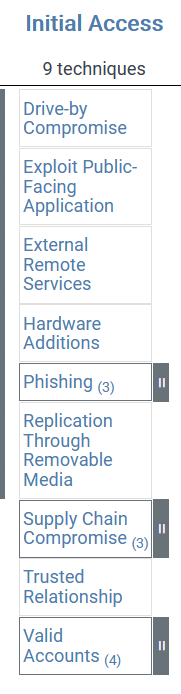
Your friends, business associates etc. have likely all got stories of either negative impact or near misses with phishing so hopefully you understand that this is a real and active threat.
Key Questions
We now know what the problem is, we know it’s real, we know the criminals use phishing in many incidents so what questions do we need to think about?
- Do we have adequate investment in ingress email controls?
- Do you have mail security such as SPF, DKIM, DMARC deployed?
- Does your organisation have MS-MTA configured?
- Are email services using encryption (TLS)?
- Are insecure email services exposed to the internet?
- Has Multi-Factor Authentication been deployed for email access?
- Do we have appropriate logging to track mail flow and mailbox access?
- Do we have sufficient controls to block common vectors such as blocking likely malicious attachments (e.g., macro enabled documents, virtual hard disk images etc.)
- Do we have sufficient client controls such as: Antivirus, Endpoint Detection and Response?
- Have we blocked macros from running where not absolutely required?
- Do we have PC device logging centrally?
- Do we have web content filtering to protect against known phishing links?
- Do we have protective DNS to protect from known phishing sites?
- Are staff trained to report phishing links to IT or the Security team?
- Are staff aware of common threats?
- Do we provide an environment that doesn’t totally fail on the chance that a good meaning member of staff accidently clicks a malicious link?
- Do you test controls on a regular basis?
- Phishing simulations should be considered with great care, using them to embarrass people is a quick-fire way to get people to NOT report incidents and generally erode morale.
- CBT training can be useful but it’s not for everyone
- Training and educating people are important but so is providing a safe environment with defence in depth
These are some of the key questions. This is such a key exploited area it’s important that as a business leader you get this checked, tested, and validated.
Summary
Ok so we’ve got a load of questions to start the ball rolling about email security. There’s a lot of consider and the above is just a sample, however hopefully it’s food for thought. Being a business leader, you are going to be a likely target for spear phishing and impersonation, making sure your organisation has people, process and technical capabilities in this space is key to help protect, detect and respond to modern day cyber threats!
References
There’s some great guidance from NCSC on email security: https://www.ncsc.gov.uk/collection/email-security-and-anti-spoofing









