Leadership
Leadership
The Security Challenges of 2021
The gaps between strategic security improvement and keeping the wolves out, today!
The Cyber Realities in 2021
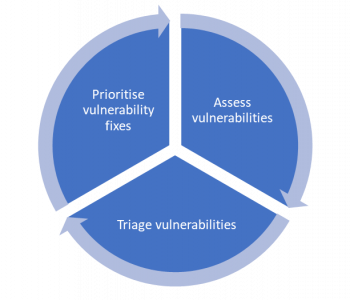
Most organisations today honestly don’t have great cyber security postures. Cyber security has improved since the 80’s and 90s’s but still common gaps can be found in the same old areas.
So, whilst security possibilities and technical capabilities for defence have greatly improved, this hasn’t really translated into the level of change we would like to see on the ground inside organisations.
I’m writing this post after giving a talk today about the challenges I see in cyber security across different organisations but also after watching a talk by Dave Kennedy which from my perspective emulates my experiences and largely my views. Read more “The Security Challenges of 2021”