 Defense
Defense
If you know me that one of the first things, I recommend organisations do is conduct password audits against active directory on a regular basis. There are a ton of ways to do this and depending upon size of directory and budget you will likely want to do this with more than a CPU however the process remains the same. So, with the news that a new release of L0phtcrack (open source) is online let’s take a look at how we can deploy and start cracking those hashes! This isn’t an end to end guide to cracking with l0phtcrack – but it does show the install process and provide considerations for your cracking adventures. Remember, only do this where you have authorisation.
Getting Started
Ok so we need to download the binaries (this is a Windows tool) from: https://gitlab.com/l0phtcrack/l0phtcrack.gitlab.io/-/tree/main/public/releases/7.2.0
Once we have setup downloaded, from an elevated position let’s open the setup executable.
Click INSTALL
Click FINISH
Cracking some hashes
On our first run we have the wizard appear.
Let’s launch the wizard
Click NEXT
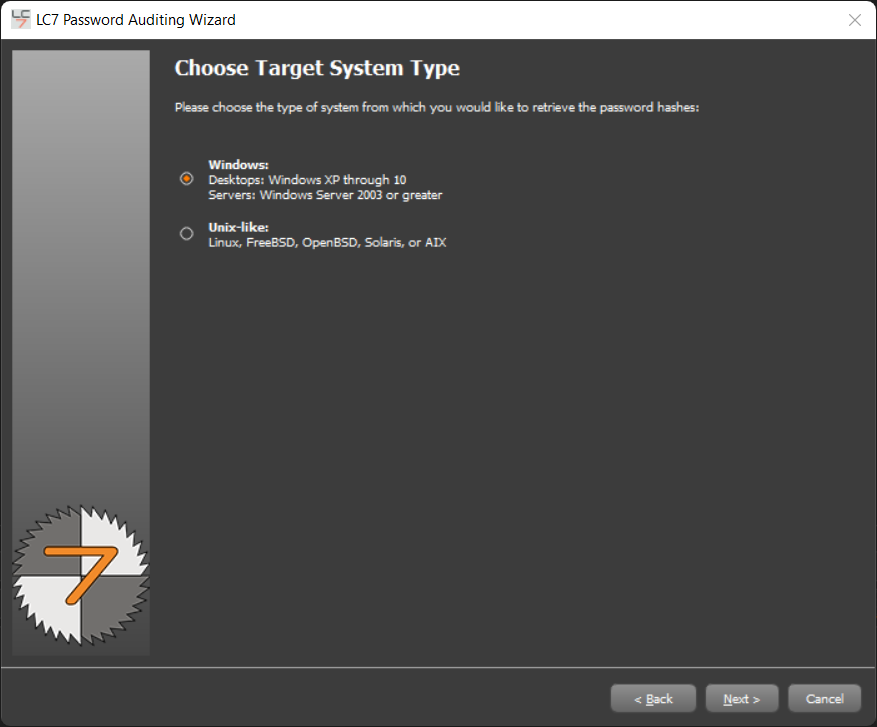
Now we can choose the target type:
Windows
or
UNIX-Like
We are going to audit a Windows machine.
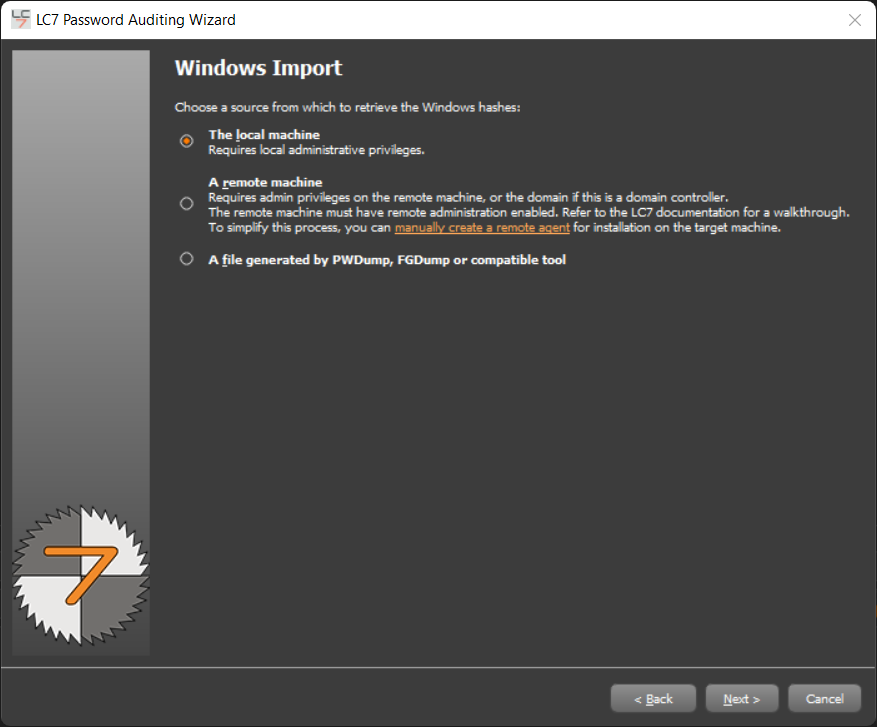
We can do this via a few means, from the local system, from a remote system (using a Windows Agent/Service) or from a password dump file.
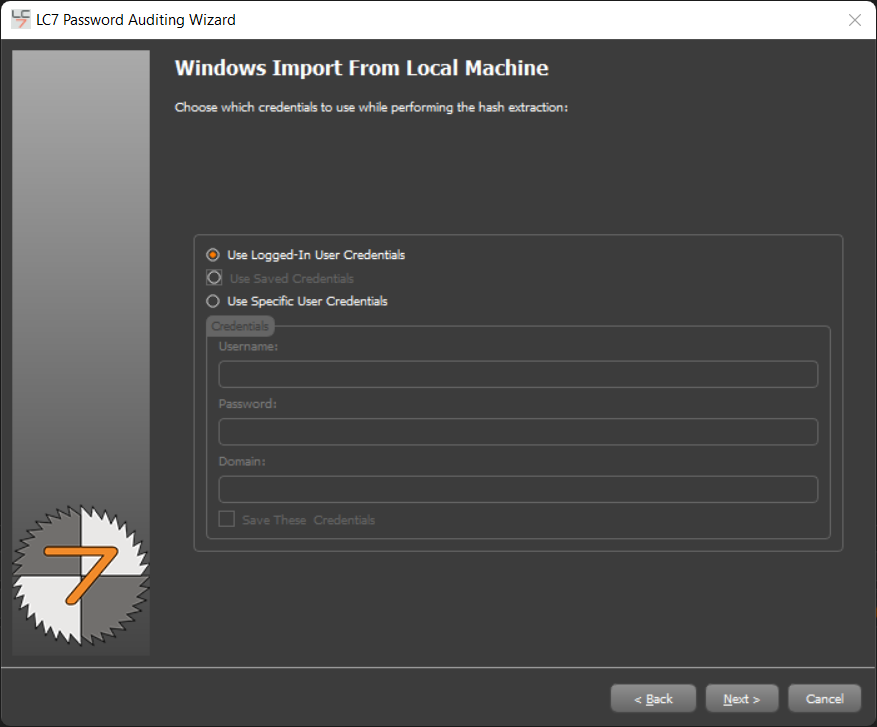
We are going to audit the local system:
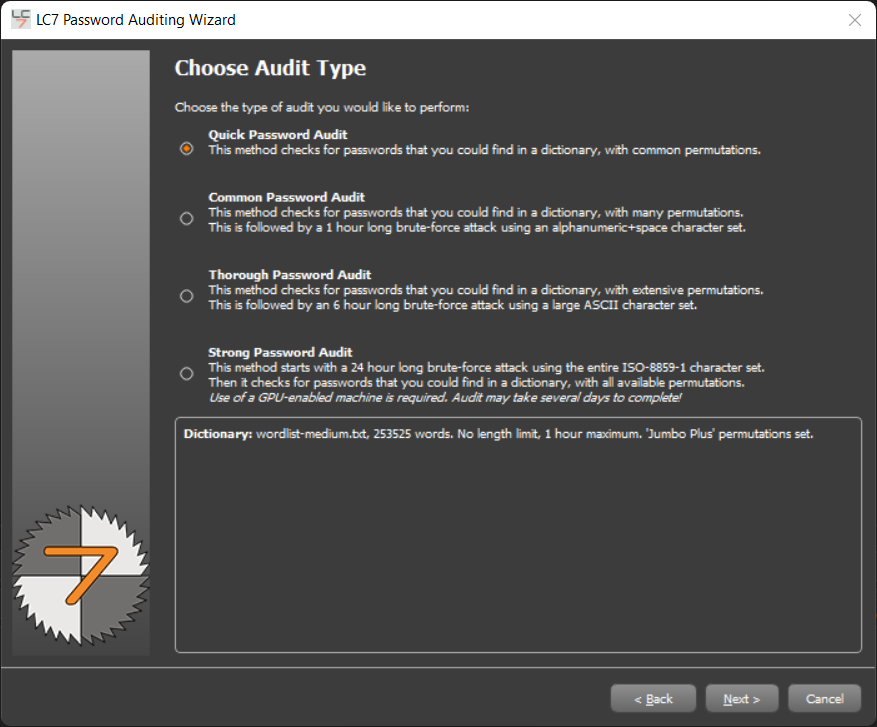
Since this is a demo we are going to use the Quick Password Audit feature.
Click NEXT
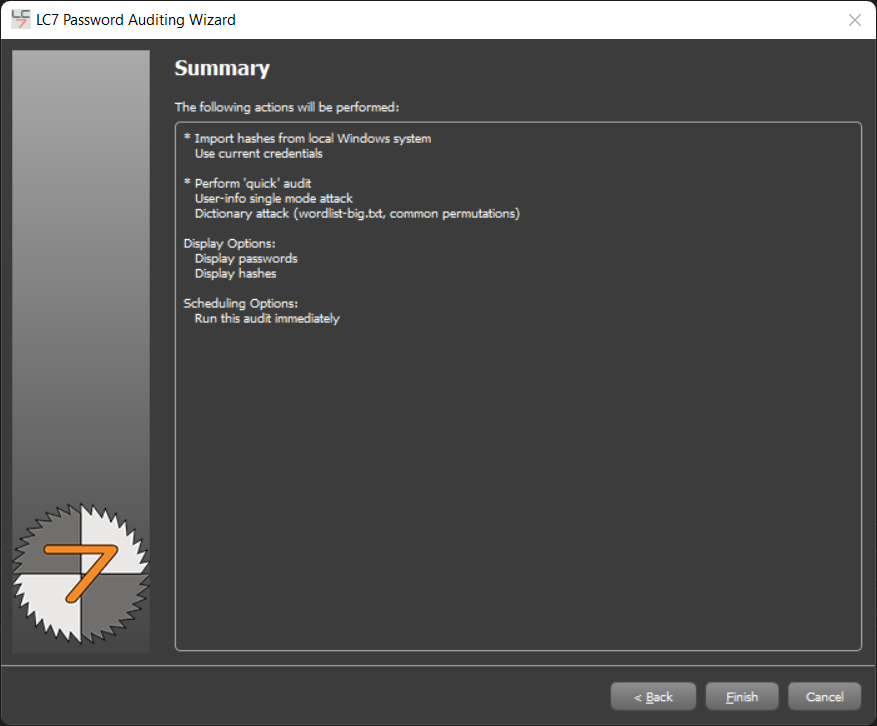
Now the sessions will start:
Once the hashes a cracking run will begin. One thing you will learn about hash cracking is that one attempt is generally never enough. You will want to try a range of approaches to wordlist generation and mangling/character substitution.
Considerations
Ok there are several things to consider:
- You will need admin rights on the targets
- You will need GPUs if you want to do this in anger
- You may need to ensure antivirus exclusions are in place
- You should consider the sensitive nature of the exercise and take appropriate measures to secure the data in transit and at rest.
- You will want to ensure good controls are used to secure the outputs
Password Cracking Tips
Ok so there are a few wordlists included but let’s think about password cracking:
- Define the objectives
- You may have a time/resource constraint on cracking runs
- You may want to identify specific and sensitive accounts e.g., service accounts and domain admins etc.
- You may want to gain access to much bigger wordlists
- You will want to mangle words (there are rules in L0phcrack to do this)
- When you crack hashes feed the cleartext back into the process
- Experiment with different approaches
- Generate custom wordlists based on the target organisation, people and geography/cultures
References
https://twitter.com/L0phtCrackLLC
https://gitlab.com/l0phtcrack/l0phtcrack.gitlab.io/-/tree/main/public/releases/7.2.0






