 Defense
Defense
Vulnerability Management – Actually doing it!
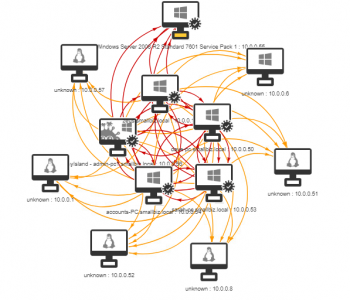
Vulnerability Management, Assessments and Vulnerability scanning is sometimes treated a with distain in the Offensive security community, I personally don’t understand that. Vulnerability management is key to inputting into security strategy, architecture, and operations. It’s coupled heavily to many other processes such as:
- Asset Management
- Risk Management
- Patch Management
- Change & Release Management
- Security Testing
- Security Monitoring
Before we start deploying let’s think about some areas for consideration when performing vulnerability scans:
- Scope
- Asset/Hosts
- IP Ranges
- Hostnames
- Connectivity
- VPNs
- LAN/WAN
- Device Types and Configuration
- Domain
- Workgroup
- Appliance
- ICS
- Printers
- Network Equipment
- Unauthenticated View
- Authenticated View
- Auth Types
- Protocols
- Scheduling
- Authority to execute
- Asset/Hosts
- Impact
- Performance
- Availability
- Confidentiality
- Objectives and Outcomes
- Reporting
- Information Flow
- Report Storage and Confidentiality